My File Server: 1 Walkthrough Vulnhub CTF My File Server: 1 Walkthrough Vulnhub CTF I will share with you a…
Performing Rule Based Attack Using Hashcat This post will focus on Performing Rule Based Attack Using Hashcat. It’s a way…
Password Cracking with Hashcat Hello Friends, Today I’m going to explain the Hashcat password Cracking Tool, As I learn from…
Introduction of Mobile Forensic Today’s smartphones are used less for calling and more for socializing. This has resulted in smartphones…
Attacking & Exploitation Before starting with this blog firstly visit wordpress enumeration blog . Researchers discovered an ongoing malvertising (online…
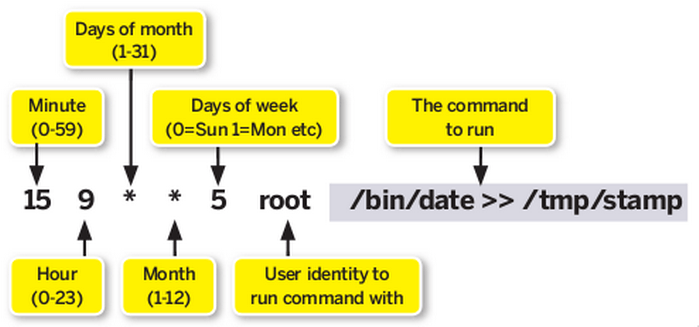
In this blog I will share procedure to enumerate and exploit Cronjob. Before going for exploitation of cronjob we are…
WordPress User Enumeration These 10 enumeration techniques are a very fast way to identify users of a WordPress installation. With…
Netcat is a featured networking utility tool which reads and writes data across network connections, using the TCP/IP protocol. It…
Network Mapper (Nmap) also known as the God of Port Scanners used for network discovery and the basis for most…
Whatsapp Hacking and Security – Cyber Crime Capsule Course at Police Radio Training School