Password Cracking with Hashcat
Hello Friends, Today I’m going to explain the Hashcat password Cracking Tool, As I learn from my cybersecurity classes and reading some blogs doing practices and the help of infosec boy’s able to explain it, so obviously the credits goes to Armour Infosec. Password cracking and user account exploitation is one of the most issues in cybersecurity field. Password Cracking tools, like Hashcat and John the Ripper, Provide the potential attackers to check billions of passwords per second against Victim’s password hashes. these tools have proved to be effective in cracking passwords, recent research shows that combining deep learning techniques with these tools can produce significantly better results. Specifically, using Generative Adversarial Networks (GANs), which comprises of two neural networks, to generate high-quality password guesses can improve the existing tools to match 51%-73% more passwords than just the tools alone. This significant improvement demonstrates that this new approach using deep learning can generate numerous new pass-words that were once beyond the reach of other tools.On one hand, this is an impressive result driven by researchers of deep learning and cybersecurity, and on the other, a strong warning to the community of the increasing dangers of weak password authentication.
This blog is a reference guide for cracking, tool usage and supportive.tools that assist pentesters in password recovery (cracking). this will not be covering the installation of these tools but will include references to their proper installation, and if all else fails, Google. Updates and additions to this blog are planned yearly as advancements in cracking evolve.
“Password recovery is a battle against math, time, cost, and human behavior, and much like any battle, the tactics are constantly evolving.”
Table of content
- Required Software
- Core Hash Cracking Knowledge
- Cracking Methodology
- Basic Cracking
- Dictionary / Wordlist
- Rules & Masks
- Common Hash Examples
- Appendix
- Online Resources
- Hashcat Menu
- Hash Cracking Benchmarks
- Hash Cracking Speed
REQUIRED SOFTWARE
In order to follow many of the techniques in this manual, you will need to install the following software on your UNIX host. This book does not cover how to install said software and assumes you were able to follow the included links and extensive support websites.
HASHCAT v5.1.0 (or newer)
https://hashcat.net/hashcat/
JOHN THE RIPPER 1.9.0-jumbo-1 (or newer)
https://www.openwall.com/john/
Hashcat-utils v1.9 (or newer)
https://hashcat.net/wiki/doku.php?id=hashcat_utils
Additionally you will need dictionaries/wordlists and highly recommend the below sources:
WEAKPASS DICTIONARY
https://weakpass.com/wordlist
CRACKSTATION DICTIONARY
https://crackstation.net/buy-crackstation-wordlist-password-cracking-dictionary.htm
SKULL SECURITY WORDLISTS
https://wiki.skullsecurity.org/index.php?title=Passwords
Throughout the manual, generic names have been given to the various inputs required in a cracking
commands structure. Legend description is below:
COMMAND STRUCTURE LEGEND
hashcat = Generic representation of the various Hashcat binary names (hashcat tool)
john = Generic representation of the John the Ripper binary names (John tool)
#type = Hash type; which is an abbreviation in John or a number in Hashcat (hash MD5,MD4..)
hash.txt = File containing target hashes to be cracked (Raw hash list )
dict.txt = File containing dictionary/wordlist (password list)
rule.txt = File containing permutation rules to alter dict.txt input
passwords.txt = File containing cracked password results
outfile.txt = File containing results of some functions output
Lastly, as a good reference for testing various hash types to place into your “hash.txt” file, the below
sites contain all the various hashing algorithms and example output tailored for each cracking tool:
HASHCAT HASH FORMAT EXAMPLES
https://hashcat.net/wiki/doku.php?id=example_hashes
JOHN THE RIPPER HASH FORMAT EXAMPLES
http://pentestmonkey.net/cheat-sheet/john-the-ripper-hash-formats
http://openwall.info/wiki/john/sample-hashes
CORE HASH CRACKING KNOWLEDGE-:
ENCODING vs HASHING vs ENCRYPTING
Encoding = transforms data into a publicly known scheme for usability
Hashing = one-way cryptographic function nearly impossible to reverse
Encrypting = mapping of input data and output data reversible with a key
CPU vs GPU
CPU = 2–72 cores mainly optimized for sequential serial processing
GPU = 1000’s of cores with 1000’s of threads for parallel processing
CRACKING TIME = KEYSPACE / HASHRATE
Keyspace: charset^length (?a?a?a?a = 95⁴ = 81,450,625)
Hashrate: hashing function / hardware power (bcrypt / GTX1080 = 13094 H/s)
Cracking Time: 81,450,625 / 13094 H/s = 6,220 seconds
*Keyspace displayed and Hashrate vary by tool and hardware used.
SALT = random data that’s used as additional input to a one-way function
ITERATIONS = the number of times an algorithm is run over a given hash
HASH IDENTIFICATION
“there isn’t a foolproof method for identifying which hash function was used by simply looking at the hash, but there are reliable clues (i.e. $6$ sha512crypt).The best method is to know from where the hash was extracted and identify the hash function for that software”
DICTIONARY/WORDLIST ATTACK = straight attack uses a precompiled list of words, phrases,
and common/unique strings and Might be genrated according to the Information gathered to attempt to match a password.
BRUTE-FORCE ATTACK = attempts every possible combination of a given character set, usually up
to a certain length.(work like the probability mathod to make combinations)
RULE ATTACK = generates permutations against a given wordlist by modifying, trimming,
extending, expanding, combining, or skipping words.
MASK ATTACK = a form of targeted brute-force attack by using placeholders for characters in certain
positions (i.e. ?a?a?a?l?d?d).
HYBRID ATTACK = combines a Dictionary and Mask Attack by taking input from the dictionary and
adding mask placeholders (i.e. dict.txt ?d?d?d).CRACKING RIG = from a basic laptop to a 64 GPU cluster, this is the hardware/ platform
on which you perform your password hash attacks.
EXPECTED RESULTS
Know your cracking rig’s capabilities by performing benchmark testing and don’t assume you can
achieve the same results posted by forum members without using the exact same dictionary, attack plan,
or hardware setup.Cracking success largely depends on your ability to use resources efficiently and
make calculated trade-offs based on the target hash.
DICTIONARY/WORDLIST vs BRUTE-FORCE vs ANALYSIS
Dictionaries and brute-force are not the end all be all to crack hashes.They are merely the beginning and end of an attack plan.I’ll say True mastery is everything in the middle,where analysis and information gathering of passwords,patterns, behaviors, and policiesaffords the ability to recover that last 20%. Experiment with your attacks and research and compile targeted wordlists with your new knowledge.Do not rely heavily on dictionaries because they can only help you with what is “known” and not the unknown.In realworld Analysis of target and gather information to make your own dictionary/wordlist is best way to attack and get credentials of the target easier and faster.
CRACKING METHODOLOGY
Following is basic cracking methodology broken into steps,but the process is subject to change based on current/future target information uncovered during the cracking process.
1 – EXTRACT HASHES
Pull hashes from target,Victim Machine,identify hashing function, and properly format output for your tool of choice.
2 – FORMAT HASHES
Format your hashes based on your tool’s preferred method.See tool documentation for this guidance.
Hashcat,for example,on each line takes <user>:<hash> OR just the plain <hash>.
3 – EVALUATE HASH STRENGTH
Using the Appendix table “Hash Cracking Speed (Slow-Fast)” assess your target hash and it’s cracking
speed.If it’s a slow hash,you will need to be more selective at what types of dictionaries and attacks
you perform.If it’s a fast hash,you can be more liberal with your attack strategy.
4 – CALCULATE CRACKING RIG CAPABILITIES
With the information from evaluating the hash strength,baseline your cracking rig’s capabilities.
Perform benchmark testing using John The Ripper and/or Hashcat’s built-in benchmark ability on your
rig,it’s totally depends on your hardware.for example have a look..!
Hash Crackers/Bit Coin Miners
Fast Hash One
• 1.536TH/s – Cost 3-5,000 dollars.
25 GPU Hash Cracker
• An eight character NTLM password
cracked in 5.5 hours. 14 character LM
hash cracked in six minutes.350 billion
hashes per second.
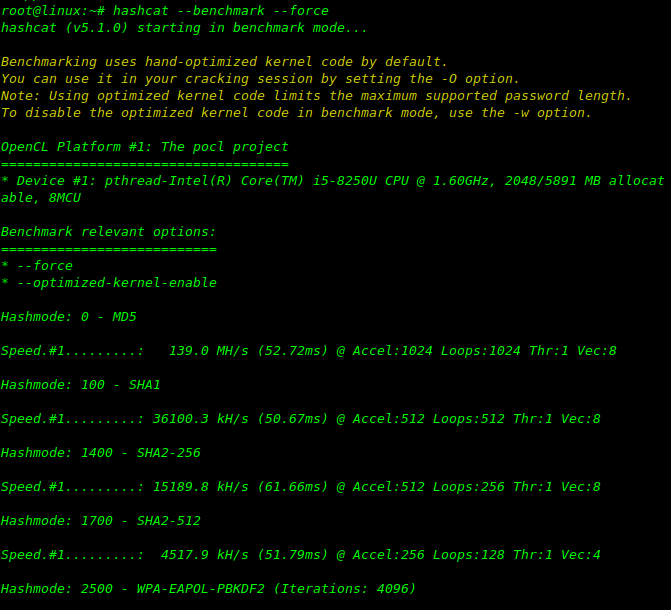
To know about your System capability,use these command to get the result.
hashcat --benchmark --force hashcat -b -m 0 --force
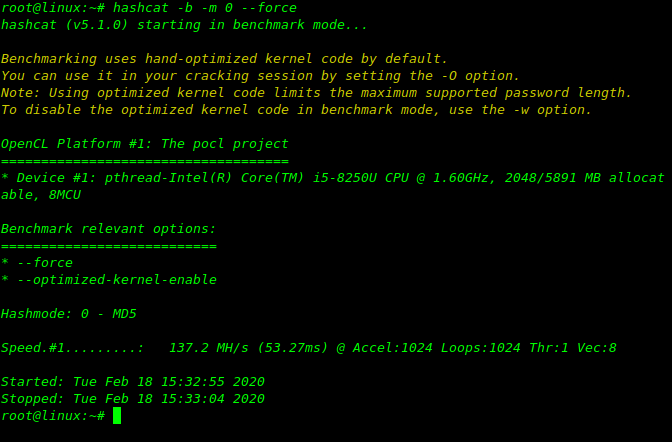
Based on these results you will be able to better assess your attack options by knowing your rigs capabilities against a specific hash. This will be a more accurate result of a hash’s cracking speed based on your rig.It will be useful to save these results for future reference.
5 – FORMULATE PLAN
Based on known or unknown knowledge begin creating an attack plan.Included on the next page is a
“Basic Cracking” to get you started.
6 – ANALYZE PASSWORDS
After successfully cracking a sufficient amount of hashes analyze the results for any clues or patterns.
This analysis may aid in your success on any remaining hashes.
7 – CUSTOM ATTACKS
Based on your password analysis create custom attacks leveraging those known clues or patterns.
Examples would be custom mask attacks or rules to fit target users’ behavior or preferences.just by doing some social engineering and footprinting or depends on your knowldge.
8 – ADVANCED ATTACKS
Experiment with Princeprocessor, custom Markov-chains, maskprocessor, or custom dictionary attacks
to shake out those remaining stubborn hashes. This is where your expertise and creativity really come
into play.
9 – REPEAT
Go back to STEP 4 and continue the process over again, tweaking dictionaries, mask, parameters, and
methods.gather some more information about,You’re in the grind at this point and need to rely on skill and luck.
Basic-cracking
This is only meant as a basic guide to processing hashes and each scenario will obviously be unique
based on external circumstances.For this attack plan we will assume we know the password hashes are
raw MD5 and assume we have already captured some plain text passwords of users.If we had no
knowledge of plain text passwords we would most likely skip to DICTIONARY/WORDLIST attacks.
Lastly,since MD5 is a “Fast” hash we can be more liberal with our attack plan.
1 – CUSTOM WORDLIST
First compile your known plain text passwords into a custom wordlist file.Pass this to your tool of
choice as a straight dictionary attack.
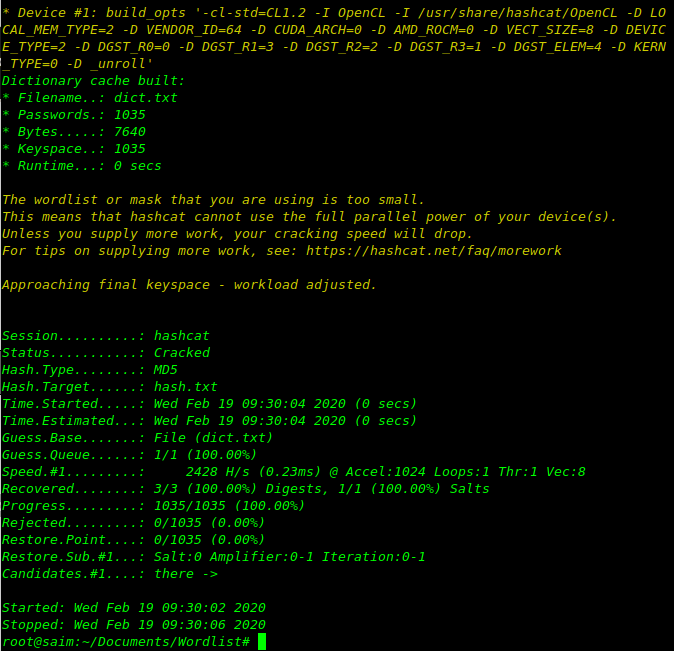
hashcat -a 0 -m 0 -w 4 hash.txt custom_list.txt hashcat -a 0 -m 0 -w 4 hash.txt pass.txt --force
This will work only for MD5 hash where:-
-a 0 designates a dictionary attack
-m 0 designates the type of hash we are cracking (MD5)
-w 4 workload profile
-o cracked.txt is the output file for the cracked passwords.
hash.txt is our input file of hashes.
custom_list.txt is the wordlist file for this dictionary attack.
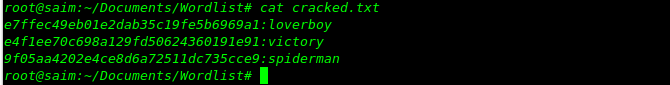
After cracking the output file will show you the passwords of cracked hashes like down below…
2 – CUSTOM WORDLIST + RULES
Run your custom wordlist with permutation rules to crack slight variations.Rules will help you to get password sooner as you have the information about victim hash.follow this link to know more about rule based attack.after all this is rockyou.txt not custom wordlist you can use according to your victim.
https://www.armourinfosec.com/performing-rule-based-attack-using-hashcat/
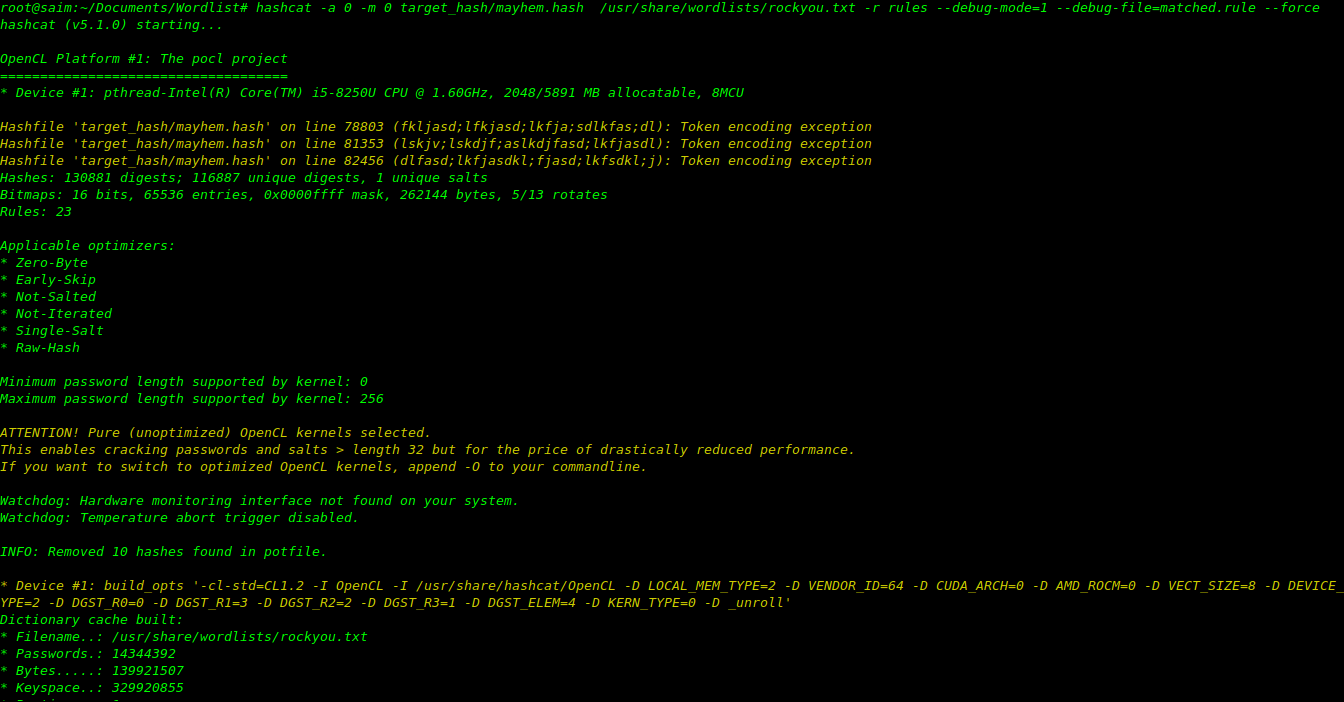
hashcat -a 0 -m 0 target_hash/mayhem.hash /usr/share/wordlists/rockyou.txt -r rules --debug-mode=1 --debug-file=matched.rule --force
3 – DICTIONARY/WORDLIST
Perform a broad dictionary attack, looking for common passwords and leaked passwords in well known
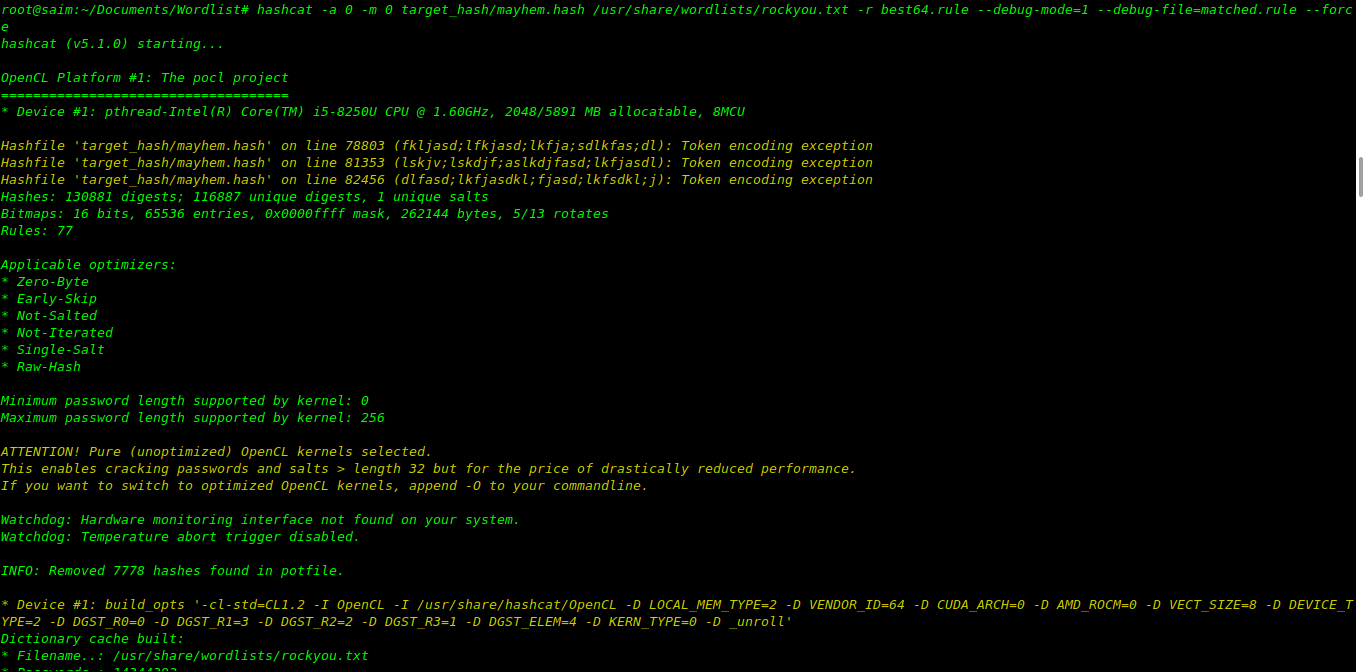
dictionaries/wordlists.I’m using best64.rule of hashcat and rockyou.txt to crack.
hashcat -a 0 -m 0 target_hash/mayhem.hash /usr/share/wordlists/rockyou.txt -r best64.rule --debug-mode=1 --debug-file=matched.rule --force
4 – DICTIONARY/WORDLIST + RULES
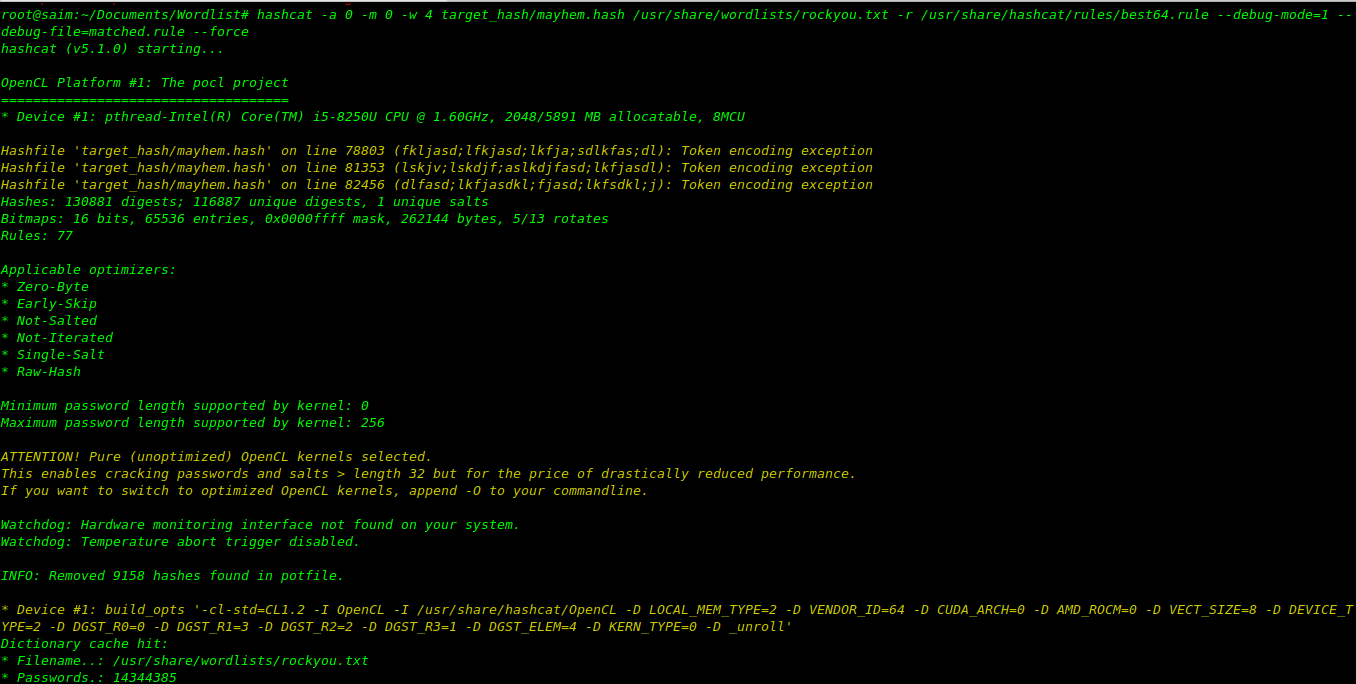
Add rule permutations to the broad dictionary attack, looking for subtle changes to common words/phrases and leaked passwords.
hashcat -a 0 -m 0 -w 4 target_hash/mayhem.hash /usr/share/wordlists/rockyou.txt -r /usr/share/hashcat/rules/best64.rule --debug-mode=1 --debug-file=matched.rule --force
for the output open matched.rule to which rules are worked.
5 – CUSTOM WORDLIST + RULES
Add any newly discovered passwords to your custom wordlist and run an attack again with permutation
rules, looking any other variations,just by hitting the echo or awk to append the new rule.and then use the above command.
:: awk -F “:” ‘{print $2}’ hashcat.potfile >> custom_list.txt
6 – MASK
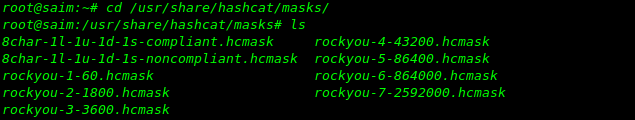
Now we will use mask attacks included with Hashcat to search the keyspace for common password
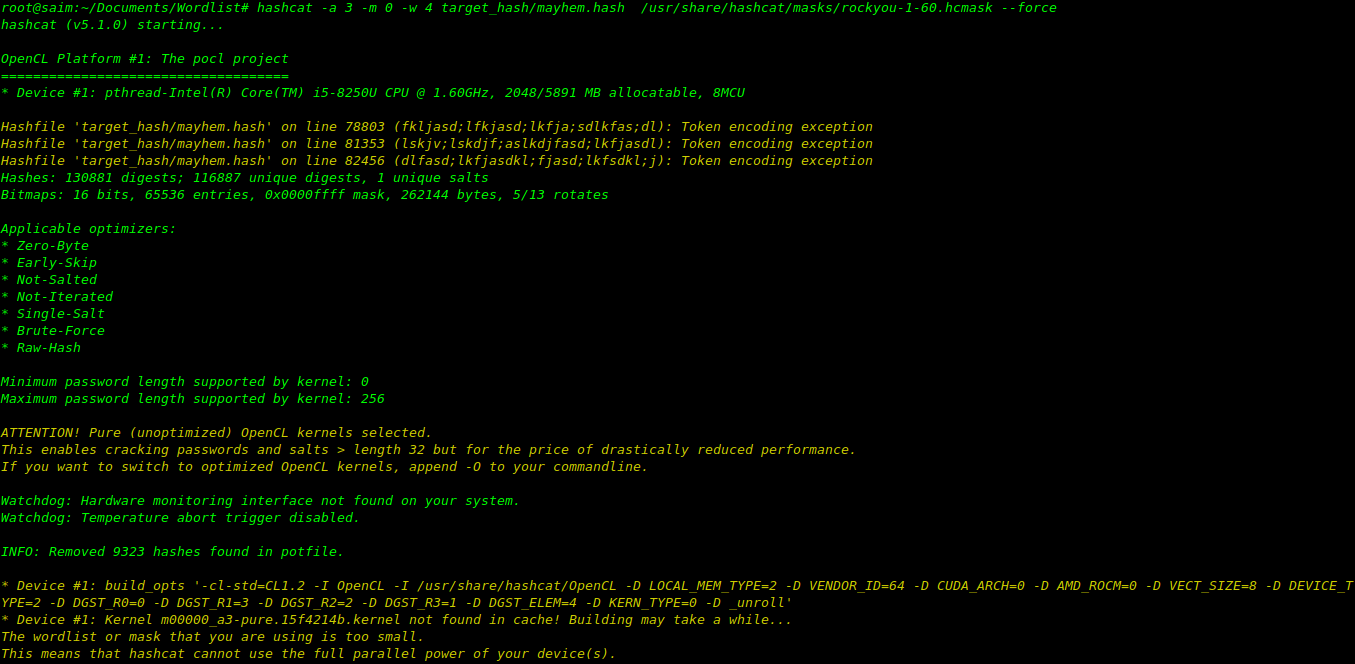
lengths and patterns, based on the RockYou dataset.there’s many pattern of passwords inside the rockyou-1-6-.hcmask like our rule based attack.go to the link to find all paths of hashcat https://centos.pkgs.org/6/forensics-i386/hashcat-3.00-1.el6.i686.rpm.html Already stored masks of hashcat.(note: attack mode will be change -a 0 to -a 3)
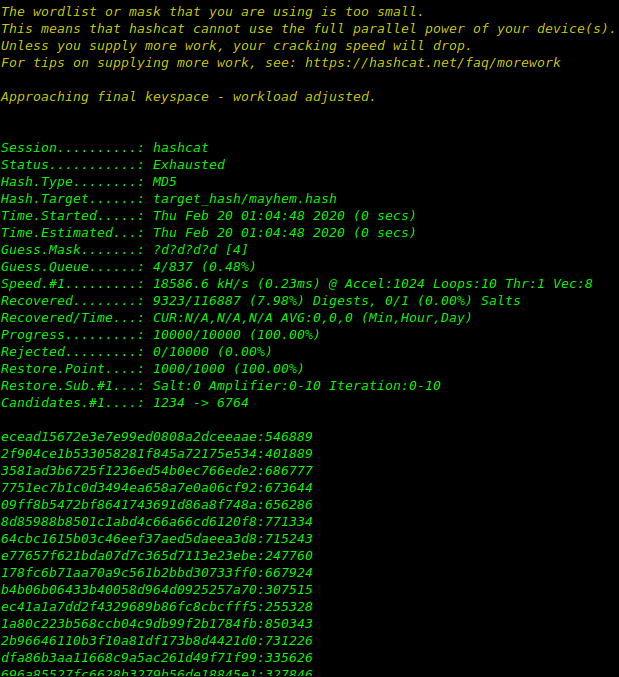
hashcat -a 3 -m 0 -w 4 target_hash/mayhem.hash /usr/share/hashcat/masks/rockyou-1-60.hcmask --force
The list of all recovered passwords of given hashes.
7 – HYBRID DICTIONARY + MASK
Using a dictionary of your choice, conduct hybrid attacks looking for larger variations of common words or known passwords by appending/prepending masks to those candidates.now i think you’re able to run the commands according to needs.can’t show you all the output screen shots.there’s lots more i have to cover in this blog so lets move on to the next..
hashcat -a 7 -m 0 -w 4 hash.txt rockyou-1–60.hcmask dict.txt hashcat -a 6 -m 0 -w 4 hash.txt dict.txt rockyou-1-60.hcmask
8 – CUSTOM WORDLIST + RULES
Add any newly discovered passwords back to your custom wordlist and run an attack again with
permutation rules looking any other subtle variations.
awk -F “:” ‘{print $2}’ hashcat.potfile >> custom_list.txt
hashcat -a 0 -m 0 -w 4 hash.txt custom_list.txt -r dive.rule --loopback
9 – COMBO
Using a dictionary of your choice, perform a combo attack by individually combining the dictionary’s
password candidates together to form new candidates.just mean combinig to dictionary’s to crack the hash.
hashcat -a 1 -m 0 -w 4 hash.txt dict.txt dict.txt
10 – CUSTOM HYBRID ATTACK
Add any newly discovered passwords back to your custom wordlist and perform a hybrid attack against
those new acquired passwords.
awk -F “:” ‘{print $2}’ hashcat.potfile >> custom_list.txt
hashcat -a 6 -m 0 -w 4 hash. txt custom_list.txt rockyou-1-60.hcmask
hashcat -a 7 -m 0 -w 4 hash. txt rockyou-1-60.hcmask custom_list.txt
11 – CUSTOM MASK ATTACK
By now the easier, weaker passwords may have fallen to cracking, but still some remain.Using PACK
create custom mask attacks based on your currently cracked passwords. Be sure to sort out
masks that match the previous rockyou-1-60.hcmask list. hashcat -a 3 -m 0 -w 4 hash.txt custom_masks.hcmask
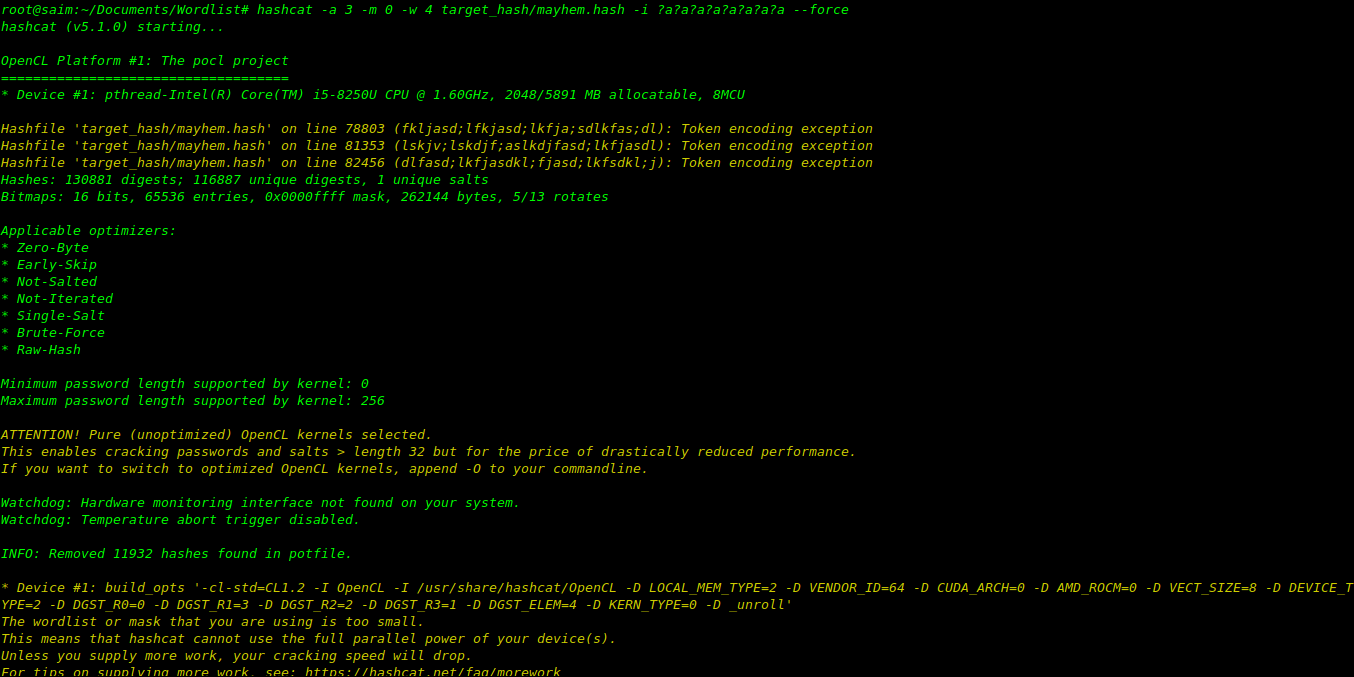
12 – BRUTE-FORCE
When all else fails begin a standard brute-force attack, being selective as to how large a keyspace your
rig can adequately brute-force. Above 8 characters this is typically pointless due to hardware limitations
and password entropy/ complexity.This particular mask will attempt to bruteforce an 8 character password.
Hashcat has the following charsets built-in:
?l = abcdefghijklmnopqrstuvwxyz (lowercase)
?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ(uppercase)
?d = 0123456789(digits)
?h = 0123456789abcdef(digit+lowercase)
?H = 0123456789ABCDEF(d+u)
?s = «space»!"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ (special char)
?a = ?l?u?d?s (all alpha + lwrc + digit + special char)
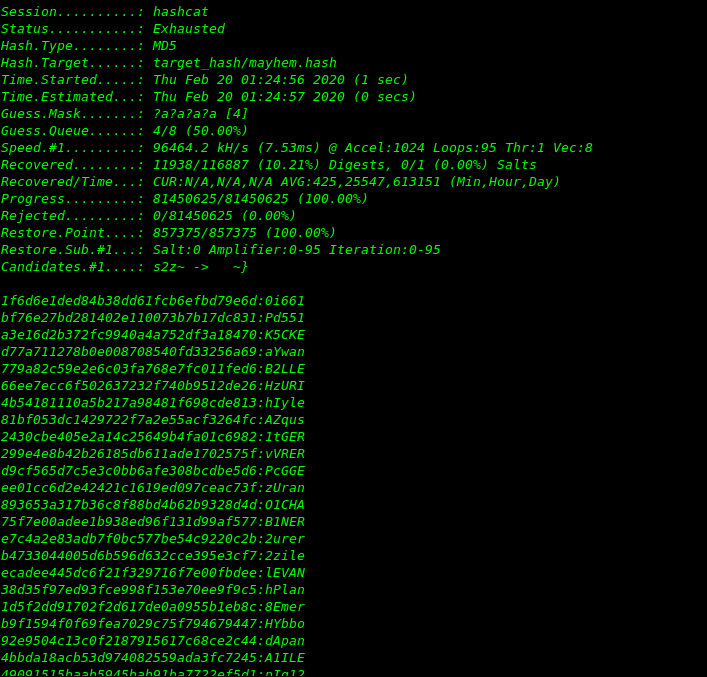
hashcat -a 3 -m 0 -w 4 target_hash/mayhem.hash -i ?a?a?a?a?a?a?a?a --force
ONLINE PASSWORD ANALYSIS RESOURCES
WEAKPASS
Analyzes public password dumps and provides efficient dictionaries for download.
http://weakpass.com/
PASSWORD RESEARCH
Important password security and authentication research papers in one place.
http://www.passwordresearch.com/
THE PASSWORD PROJECT
Compiled analysis of larger password dumps using PIPAL and PASSPAL tools.
http://www.thepasswordproject.com/leaked_password_lists_and_dictionaries
DICTIONARY / WORDLIST
DOWNLOAD RESOURCES
WEAKPASS
http://weakpass.com/wordlist
CRACKSTATION DICTIONARY
https://crackstation.net/buy-crackstation-wordlist-password-cracking-dictionary.htm
HAVE I BEEN PWNED
*You’ll have to crack the SHA1’s
https://haveibeenpwned.com/passwords
SKULL SECURITY WORDLISTS
https://wiki.skullsecurity.org/index.php?title=Passwords
CAPSOP
https://wordlists.capsop.com/
UNIX-NINJA DNA DICTIONARY
*Dictionary link at bottom of article*
https://www.unix-ninja.com/p/Password_DNA
PROBABLE-WORDLIST
https://github.com/berzerk0/Probable-Wordlists
EFF-WORDLIST
Long-list (7,776 words) & Short-list (1,296 words)
https://www.eff.org/files/2016/07/18/eff_large_wordlist.txt
https://www.eff.org/files/2016/09/08/eff_short_wordlist_1.txt
RAINBOW TABLES
*Rainbow Tables are for the most part obsolete but provided here for reference*
http://project-rainbowcrack.com/table.htm
TARGETED WORDLISTS
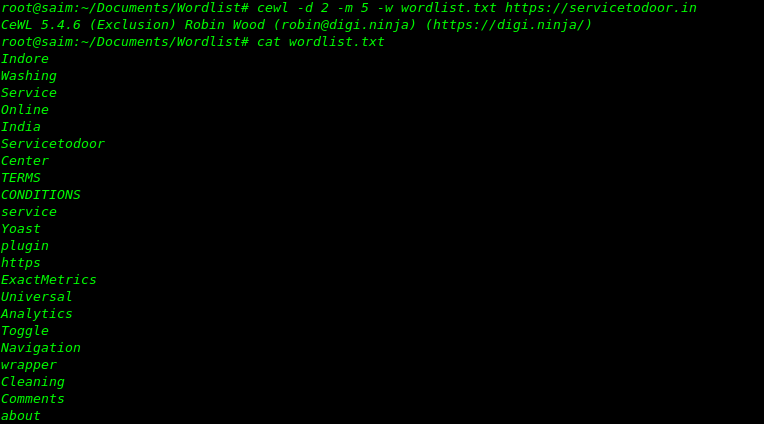
CeWL
Custom wordlist generator scrapes & compiles keywords from websites.
https://digi.ninja/projects/cewl.php
Example scan depth of 2 and minimum word length of 5 output to wordlist.txt
cewl -d 2 -m 5 -w wordlist.txt http://<target website>
SMEEGESCRAPE
Text file and website scraper which generates custom wordlists from content.
http://www.smeegesec.com/2014/01/smeegescrape-text-scraper-and-custom.html
Compile unique keywords from text file and output into wordlist.
SmeegeScrape.py -f file.txt -o wordlist.txt
Scrape keywords from target website and output into wordlist.
SmeegeScrape.py -u http://<target website> -si -o wordlist.txt
GENERATE PASSWORD HASHES
HASHCAT
https://github.com/hashcat/hashcat/tree/master/tools
test.pl passthrough <#type> <#> dict.txt
MDXFIND
https://hashes.org/mdxfind.php
echo | mdxfind -z -h ‘<#type>’ dict.txt
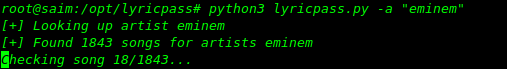
LYRICPASS (Song Lyrics Password Generator)
python3 lyricpass.py -a "eminem"
ONLINE HASH CRACKING SERVICES
GPUHASH
https://gpuhash.me/
CRACKSTATION
https://crackstation.net/
ONLINE HASH CRACK
https://www.onlinehashcrack.com/
HASH HUNTERS
http://www.hashhunters.net/
COMMON HASH EXAMPLES
MD5, NTLM, NTLMv2, LM, MD5crypt, SHA1, SHA256, bcrypt, PDF 1.4 - 1.6 (Acrobat 5-8), Microsoft OFFICE 2013, RAR3-HP, Winzip, 7zip, Bitcoin/Litecoin, MAC OSX v10.5-v10.6, MySQL 4.1-5+, Postgres, MSSQL(2012)-MSSQL(2014), Oracle 11g, Cisco TYPE 4 5 8 9, WPA PSK / WPA2 PSK
MDS (HASHCAT)
HASH FORMAT
8743b52063cd84097a65dl633f5c74f5
BRUTE FORCE ATTACK
hashcat -m 0 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 0 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 0 -a 0 hash.txt dict.txt -r rule.txt
NTLM (PWDUMP)
HASH FORMAT
b4b9b02e6f09a9bd760f388b67351e2b
BRUTE FORCE ATTACK
hashcat -m 1000 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 1000 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 1000 -a 0 hash.txt dict.txt -r rule.txt
LM
HASH FORMAT
$LM$a9c604d244c4e99d
BRUTE FORCE ATTACK
hashcat -m 3000 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 3000 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 3000 -a 0 hash.txt dict.txt -r rule.txt
MD5CRYPT
HASH FORMAT
$1$28772684$iEwNOgGugq09.bIz5sk8k/
BRUTE FORCE ATTACK
hashcat -m 500 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 500 -a 0 hash.txt dict.txtWORDLIST + RULE ATTACK
hashcat -m 500 -a 0 hash.txt dict.txt -r rule.txt
SHA1
HASH FORMAT
b89eaac7e61417341b710b727768294d0e6a277b
BRUTE FORCE ATTACK
hashcat -m 100 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 100 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 100 -a 0 hash.txt dict.txt -r rule.txt
SHA256
HASH FORMAT
127e6fbfe24a750e72930c220a8el38275656b8e5d8f48a98c3c92df2caba935
BRUTE FORCE ATTACK
hashcat -m 1400 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 1400 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 1400 -a 0 hash.txt dict.txt -r rule.txt
BCRYPT
HASH FORMAT
$2a$05$LhayLxezLhKlLhWvKxCyLOj0jlu.Kj0jZ0pEmml34uzrQlFvQDLF6
BRUTE FORCE ATTACK
hashcat -m 3200 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 3200 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 3200 -a 0 hash.txt dict.txt -r rule.txt
PDF 1.4 – 1.6 (ACROBAT 5-8)
HASH FORMAT
$pdf$2*3*128*-1028*l*16*da42eel5d4b3e08fe5b9ecea0e02ad0f*32*c9b59d72c7c670c42eeb
4fcald2cal5000000000000000000000000000000000*32*c4ff3e868dc87604626c2b8c259297al
4d58c6309c70b00afdfblfbbal0ee571
EXTRACT HASH
pdf2hashcat.py example.pdf > hash.txt
BRUTE FORCE ATTACK
hashcat -m 10500 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 10500 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 10500 -a 0 hash.txt dict.txt -r rule.txt
MICROSOFT OFFICE 2013
HASH FORMAT
example.docx:$office$*2013*100000*256*16*7dd611d7eb4c899f74816dldec817b3b*948dc0
b2c2c6c32fl4b5995a543ad037*0b7ee0e48e935f937192a59de48a7d561ef2691d5c8a3ba87ec2d
04402a94895
EXTRACT HASH
office2hashcat.py example.docx > hash.txt
BRUTE FORCE ATTACK
hashcat -m 9600 -a 3 –username hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 9600 -a 0 –username hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 9600 -a 0 –username hash.txt dict.txt -r rule.txt
RAR3-HP (ENCRYPTED HEADER)
HASH FORMAT
$RAR3$*0*45109af8ab5f297a*adbf6c5385d7a40373e8f77d7b89d317
#!Ensure to remove extraneous rar2john output to match above hash!#
EXTRACT HASH
rar2john.py example.rar > hash.txt
BRUTE FORCE ATTACK
hashcat -m 12500 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 12500 -a 0 hash.txt dict.txtWORDLIST + RULE ATTACK
hashcat -m 12500 -a 0 hash.txt dict.txt -r rule.txt
WINZIP
HASH FORMAT
$zip2$*0*3*0*b5d2b7bf57ad5e86a55c400509c672bd*d218*0**ca3d736d03a34165cfa9*$/ zip2$
#!Ensure to remove extraneous zip2john output to match above hash!#
EXTRACT HASH
zip2john.py example.zip > hash.txt
BRUTE FORCE ATTACK
hashcat -m 13600 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 13600 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 13600 -a 0 hash.txt dict.txt -r rule.txt
7-ZIP
HASH FORMAT
$7z$0$19$0$salt$8$f6196259a7326e3f0000000000000000$185065650$112$98$f3bc2a88062c
419a25acd40c0c2d75421cf23263f69c51bl3f9blaada41a8a09f9adeae45d67c60b56aad338f20c
0dcc5eb811c7a61128ee0746f922cdb9c59096869f341c7a9cblac7bb7d771f546b82cf4e6flla5e
Cd4b61751e4d8de66dd6e2dfb5b7dl022d2211e2d66eal703f96
#!Ensure to remove extraneous 7zip2john output to match above hash!#
EXTRACT HASH
7z2john.py example.7z > hash.txt
BRUTE FORCE ATTACK
hashcat -m 11600 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 11600 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 11600 -a 0 hash.txt dict.txt -r rule.txt
BITCOIN / LITECOIN
HASH FORMAT
$bitcoin$96$d011alb6a8d675b7a36d0cd2efaca32a9f8dcld57d6d01a58399ea04e703e8bbb448
99039326f7a00fl71a7bbc854a54$16$1563277210780230$158555$96$628835426818227243334
570448571536352510740823233055715845322741625407685873076027233865346542174$66$6
25882875480513751851333441623702852811440775888122046360561760525
EXTRACT HASH
bitcoin2john.py wallet.dat > hash.txt
BRUTE FORCE ATTACK
hashcat -m 11300 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 11300 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 11300 -a 0 hash.txt dict.txt -r rule.txt
MAC OS X 10.8-10.12
HASH FORMAT
username:$ml$35714$50973de90d336b5258f01e48ab324aa9ac81ca7959ac470d3d9c4395af624
398$631a0ef84081b37cfe594a5468cf3a63173cd2ec25047b89457ed300f2b41b30a0792a39912f
C5f3f7be8f74b7269ee3713172642de96ee482432a8dl2bf291a
EXTRACT HASH
sudo plist2hashcat.py /var/db/dslocal/nodes/Default/users/<username>.plist
BRUTE FORCE ATTACKhashcat -m 122 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 122 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 122 -a 0 hash.txt dict.txt -r rule.txt
MYSQL4.1 / MYSQL5+ (DOUBLE SHA1)
HASH FORMAT
FCF7C1B8749CF99D88E5F34271D636178FB5D130
EXTRACT HASH
SELECT user,password FROM mysql.user INTO OUTFILE ‘/tmp/hash.txt’;
BRUTE FORCE ATTACK
hashcat -m 300 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 300 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 300 -a 0 hash.txt dict.txt -r rule.txt
POSTGRESQL
HASH FORMAT
a6343a68d964ca596d9752250d54bb8a:postgres
EXTRACT HASH
SELECT username, passwd FROM pg_shadow;
BRUTE FORCE ATTACK
hashcat -m 12 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 12 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 12 -a 0 hash.txt dict.txt -r rule.txt
MSSQL(2012), MSSQL(2014)
HASH FORMAT
0x02000102030434ealbl7802fd95ea6316bd61d2c94622ca3812793e8fbl672487b5c904a45a31b
2ab4a78890d563d2fcf5663e46fe797d71550494be50cf4915d3f4d55ec375
EXTRACT HASH
SELECT SL.name,SL.password_hash FROM sys.sql_logins AS SL;
BRUTE FORCE ATTACK
hashcat -m 1731 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 1731 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 1731 -a 0 hash.txt dict.txt -r rule.txt
ORACLE 11G
HASH FORMAT
ac5fle62d21fd0529428b84d42e8955b04966703:38445748184477378130
EXTRACT HASH
SELECT SL.name,SL.password_hash FROM sys.sql_logins AS SL;
BRUTE FORCE ATTACK
hashcat -m 112 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 112 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 112 -a 0 hash.txt dict.txt -r rule.txt
CISCO TYPE 4 (SHA256)
HASH FORMAT
2btjjy78REtmYkkW0csHUbDZOstRXoWdX1mGrmmfeHI
BRUTE FORCE ATTACK
hashcat -m 5700 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 5700 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 5700 -a 0 hash.txt dict.txt -r rule.txt
CISCO TYPE 5 (MD5)
HASH FORMAT
$l$28772684$iEwN0gGugq09.bIz5sk8k/
BRUTE FORCE ATTACK
hashcat -m 500 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 500 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 500 -a 0 hash.txt dict.txt -r rule.txt
CISCO TYPE 9 (SCRYPT)
HASH FORMAT
$9$2MJBozw/9R3UsU$21FhcKvpghcyw8deP25G0fyZaagyU0GBymkryv0dfo6
BRUTE FORCE ATTACK
hashcat -m 9300 -a 3 hash.txt ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 9300 -a 0 hash.txt dict.txt
WORDLIST + RULE ATTACK
hashcat -m 9300 -a 0 hash.txt dict.txt -r rule.txt
WPA PSK / WPA2 PSK
HASH FORMAT
*Capture 4-way authentication handshake > capture.cap
cap2hccapx.bin capture.cap capture_out.hccapx
BRUTE FORCE ATTACK
hashcat -m 2500 -a 3 capture_out.hccapx ?a?a?a?a?a?a
WORDLIST ATTACK
hashcat -m 2500 -a 3 capture_out.hccapx dict.txt
WORDLIST + RULE ATTACK
hashcat -a 0 capture_out.hccapx dict.txt -r rule.txt
ONLINE RESOURCES
HASHCAT
https://hashcat.net/wiki/
https://hashcat.net/wiki/doku.php?id=hashcat_utilshttps://hashcat.net/wiki/doku.php?id=statsprocessor
http://www.netmux.com/blog/ultimate-guide-to-cracking-foreign-character-passwords-using-has
http://www.netmux.com/blog/cracking-12-character-above-passwords
CRACKING RIGS
http://www.netmux.com/blog/how-to-build-a-password-cracking-rig
https://www.unix-ninja.com/p/Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III
EXAMPLE HASH GENERATION
https://www.onlinehashcrack.com/hash-generator.php
https://www.tobtu.com/tools.php
http://hash.online-convert.com/
https://www.tools4noobs.com/online_tools/hash/
https://quickhash.com/
http://bitcoinvalued.com/tools.php
http://www.sha1-online.com/
http://www.freeformatter.com/hmac-generator.html
http://openwall.info/wiki/john/Generating-test-hashes
OTHER
http://blog.thireus.com/cracking-story-how-i-cracked-over-122-million-sha1-and-md5-hashed-
passwords/
http://www.utf8-chartable.de/
http://thesprawl.org/projects/pack/
https://blog.gotmilk.com/2011/06/dictionaries-wordlists/
http://wpengine.com/unmasked/
NETMUX
http://www.netmux.com
http://www.hashcrack.io
https://github.com/netmux
https://twitter.com/netmux
https://www.instagram.com/netmux/
If you’re reading this last line a huge thank’s and i’m gonna cover John the ripper to the nest blog it will contain all the screen shots of the all cracking methodology with commands and everything which left in hashcat.hope you learn something new,Thank you.