Here’s another article on Escalate My Privileges Vulnhub Walkthrough designed by Akanksha Sachin Verma for learning Linux Privilege Escalation skills….
Here is the new challenge of InfoSecWarrior CTF: 3 Walkthrough by Infosec Warrior CTF 2020. The box is designed by…
Hello everyone. This time I am sharing the walkthrough of a CTF machine designed by Akanksha Verma. This is a…
Here’s a new InfoSecWarrior CTF: 1 Walkthrough for Vulnhub machines. InfoSecWarrior CTF 2020: 01 is the first challenge of Infosec…
Here’s the new challenge of “It’s October Vulnhub Walkthrough”. It’s October is an easy box for the beginner and wannabe…
In this blog, we will learn how to install, update, remove, find packages, manage packages and repositories on Linux systems…
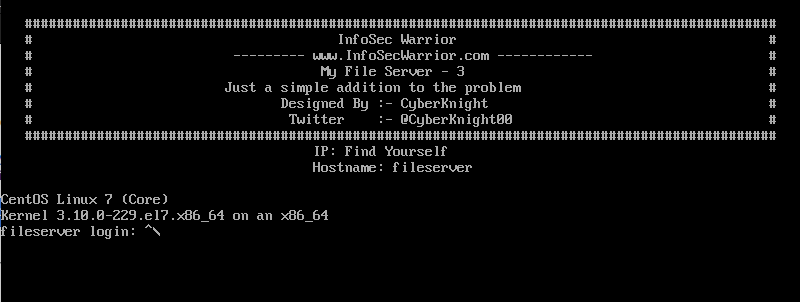
I will share with you a new Walkthrough for Infosec Warriors CTF machines. My File Server: 3 Walkthrough for the…
Often during pentests, you have a non-tty-shell there are certain commands and stuff you can’t do. This can happen if you…
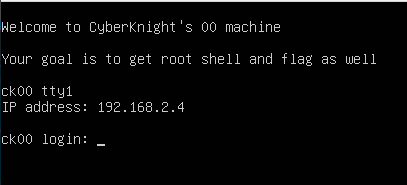
I will share with you a new Walkthrough for Vulnhub machines. CK00: Vulnhub Walkthrough for the CTF Challenge Created by…
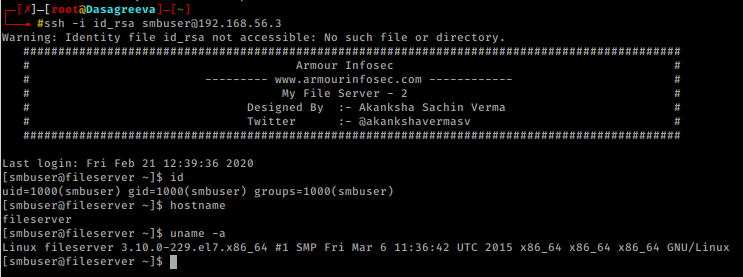
My File Server:2 Walkthrough Vulnhub CTF Download: My File Server: 2 Walkthrough Vulnhub CTF I will share with you a…