Performing Rule Based Attack Using Hashcat
This post will focus on Performing Rule Based Attack Using Hashcat. It’s a way of using a dictionary or multiple dictionaries of words in order to crack a password in Kali Linux.
Rule-based Attack
Recently I was writing a blog on hashcat to cracking the hashes but the blog was going long so i thought about to write another blog to explain more about hashcat attacks,so that you can easily crack the has.So the rule-based attack is one of the most complicated of all the attack modes.The reason for this is very simple.the rule-based attack is like a programming language designed for password candidate generation. It has functions to modify,cut or extend words and has conditional operators to skip some, etc.That makes it the most flexible,accurate and efficient attack.
Why not stick to regular expressions
Why re-invent the wheel? Simple answer: regular expressions are too slow. Typically we have to generate 1.000.000.000 (or more) fresh password candidates in less than 10 ms before hashing algorithms start to become idle, and then again and again, second after second. Just take a look at your GPU speed display to get an idea of it.
Compatibility to other rule engines
The rule-engine in hashcat was written so that all functions that share the same letter-name are 100% compatible to John the Ripper and Passwordpro rules and vice versa. Later we started to introduce some of our own functions that are not compatible. But these functions got their own letter-names to avoid conflicts.
What Are Rules and When Would I Use Them?
The first thing which comes in our mind is, What are rules why we should use rule attack to cracking the hash.So First of all, consider the following scenario. You have a basic password wordlist containing the words below:
password mysecret qwerty
If you wanted to try the above passwords with the pattern “123” added to the end, your list will become:
password password123 mysecret mysecret123 qwerty qwerty123
If you also want to capitalise the first letter of the original words, it will now become:
password password123 Password mysecret mysecret123 Mysecret qwerty qwerty123 Qwerty
Although you can type each new pattern manually for each word in your list,this will quickly get impractical with larger wordlists.
Thankfully,we can express these patterns in programming terms using rules. With rules,we can create new passwords through modification of existing passwords supplied.
Instead of having to write every new pattern for each password like above,we only require our original wordlist:
password mysecret qwerty
And a file containing the rules that express our patterns:
$c $1 $2 $3
Though much smaller, the above would produce the same outcome of words as before. Not only is this quicker than manually creating each password you want to try, your dictionary file also won’t be as large.
In short, a rule-based attack allows you to express patterns which are applied to existing passwords to quickly generate new passwords to use.and crack the hashed fast and easily.
Creating Rules
Now that we can see the benefits of rules,we will now define some rules to use in our own rule-based attack. To define our own custom set of rules to use with hashcat, we need to store them in a file,like best64.rule or something you as want.
In this tutorial,we will cover some of the most commonly used rule functions:
| Name | Function | Description | Example Rule | Input Word | Output Word |
| Nothing | : | Do nothing | : | p@ssW0rd | p@ssW0rd |
| Lowercase | l | Lowercase all letters | l | p@ssW0rd | p@ssw0rd |
| Uppercase | u | Uppercase all letters | u | p@ssW0rd | P@SSW0RD |
| Capitalize | c | Capitalize the first letter and lower the rest | c | p@ssW0rd | P@ssw0rd |
| Append Character | $X | Append character X to end | $1 | p@ssW0rd | p@ssW0rd1 |
| Prepend Character | ^X | Prepend character X to front | ^1 | p@ssW0rd | 1p@ssW0rd |
| Replace | sXY | Replace all instances of X with Y | ss$ | p@ssW0rd | p@$$W0rd |
Writing our rule-set:
To start, we will create some rules to do basic manipulation of the characters.
From the above table, we will put in our rules file the lowercase, uppercase and capitalize functions:
: l u c
The colon entry instructs hashcat to try the original word.We’ll be including this so we can compare how many passwords were cracked using unmodified passwords from the wordlist.
We’ll also append to the end of the passwords the characters one to nine individually:
$1 $2 $3 $4 $5 $6 $7 $8 $9
To express multiple functions in a single rule, you can separate them with a space like the following:
$1 $2 $3 $4
In this case we are appending characters one, two and three to the end of our passwords.(i.e. the password is root it will convert to root1234 ), And if you want to append multi combination (i.e. $5 $ 5 it will be root55)
You can substitute one character for another, by doing the following:
sXY
Where X is the character to replace and Y is the new character.
For this demonstration,we will substitute the following letters for their commonly used alternatives:
- “@” instead of “a”
- “3” instead of “e”
- “1” instead of “l”
- “0” instead of “o”
To express these as rules in a hashcat file, it looks like:
sa@ se3 sl1 sa@ se3 sl1 sa@ se3 ss&
The final rules we’ll add inserts the word “root” before and after the password:
^R ^o ^o ^t ^r ^o ^o ^t $r $o $o $t
From the above, notice we’ve also included “Root” with a capital “R” before the password.
Now that we have covered the different rules we’re going to use, make sure you have created a file called “rules” that contains the following rules
: #Lowercase l #Uppercase u #Capitalise first character c #Add '1' to the end $1 #Add '2' to the end $2 #Add '3' to the end $3 #Add '4' to the end $4 #Add '5' to the end $5 #Add '6' to the end $6 #Add '7' to the end $7 #Add '8' to the end $8 #Add '9' to the end $9 #Add '123' to the end $1 $2 $3 #Substitute 'a' for '@' sa@ #Substitute 'e' for '3' se3 #substitute 'l' for '1' sl1 #Substitute 'a' for '@', 'e' for '3', 'l' for '1' sa@ se3 sl1 #Add the word 'root' to the beginning ^R ^o ^o ^t #Add the word 'root' to the beginning ^r ^o ^o ^t #Add the word 'root' to the end $r $o $o $t
The lines beginning with a “#” are used to indicate to hashcat that the line is a comments.
Running the Rule-Based Attack
Now that we have our rules file and providing you have the Root hashes and rockyou password dictionary, we are ready to start cracking the password hashes.
In order to log the effectiveness of our rules, we’ll make use of hashcat’s debug commands. The debug option in hashcat works by logging a rule to a file every time it successfully cracks a password.
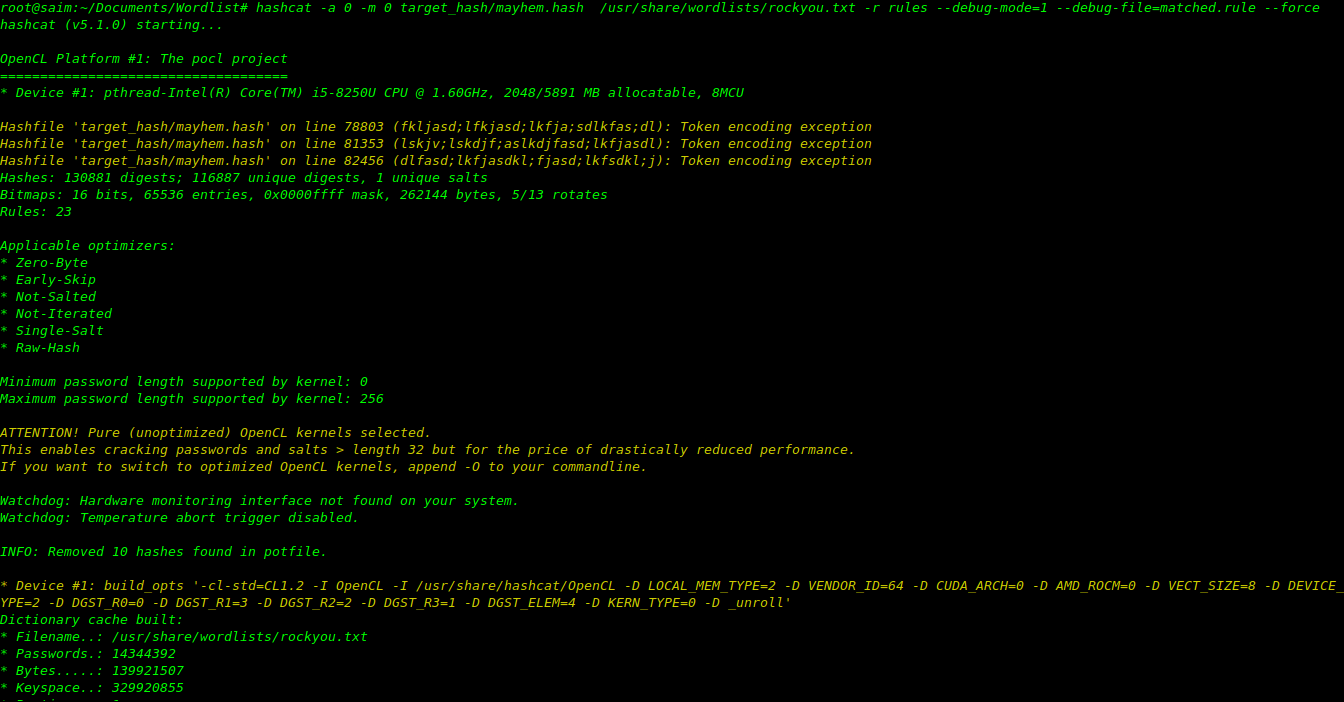
To run our rule-based attack, we will use the following command:
hashcat -a 0 -m 0 target_hash/mayhem.hash /usr/share/wordlists/rockyou.txt -r rules --debug-mode=1 --debug-file=matched.rule --force
| Argument | Meaning |
| -a 0
-m 0 |
The attack mode (Wordlist + Rule) Identify the hash as MD5.
|
| target_hash/mayhem.hash | The hash file to use. |
| /usr/share/wordlists/rockyou.txt | The rockyou wordlist. |
| -r rules | Points hashcat to our rules file called “rules”. |
| –debug-mode=1 | Writes the rule whenever it successfully cracks a password. |
| –debug-file=matched.rule
–force |
The name of the debug file where the matched rules are stored.Store every password when it cracked.
To run hashcat forcefully |
After following the steps above, when you run the command the output will look like..
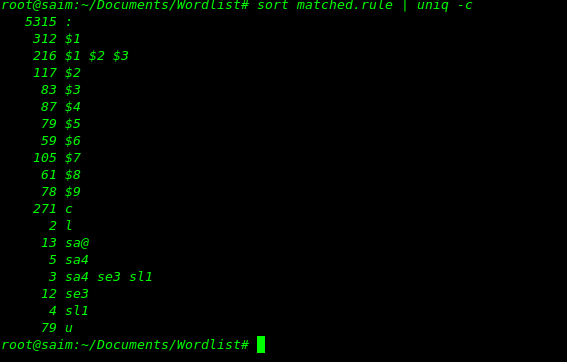
however we do not know how many passwords each rule cracked.To find this information, this is where our debug file comes in. If we look at its contents right now…
cat matched.rule sort matched.rule | uniq –c
Matched rules in cracking
So i got the output of hashes,hope this will help you to resolve queries of cracking the hash with hashcat.As previously mentioned, only the commonly used rule functions were covered in this tutorial. To view a full list of available rule functions, you can do so on the hashcat website here.Additionally recommend you to..
Using Existing Rule Files
It is worth mentioning that hashcat contains some rule files by default.These are located in the “rules” folder of your hashcat installation:
ls -l /usr/share/hashcat/rules/
Summary
In this guide, we created and used our own custom rules in hashcat to perform a rule-based attack. We started by covering what rule-based attacks are and why they are used. We then proceeded to create our own rules and use the rockyou dictionary to crack MD5 hashes.