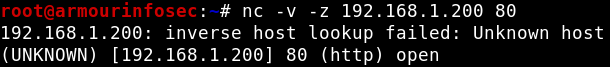Netcat is a featured networking utility tool which reads and writes data across network connections, using the TCP/IP protocol.
It is designed to be a reliable “back-end” tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities. It’s so simple, powerful, and useful that many people within the IT community refer to it as the “Swiss Army Knife of Hackers“.
Features :
- Outbound and Inbound connections, TCP or UDP, to or from any ports.
- Featured tunneling mode which allows also special tunneling such as UDP to TCP, with the possibility of specifying all network parameters (source port/interface, listening port/interface, and the remote host allowed to connect to the tunnel).
- Built-in port-scanning capabilities, with randomization
- Advanced usage options, such as buffered send-mode (one line every N seconds), and hex dump (to stderr or to a specified file) of transmitted and received data.
- Can read command line arguments from standard input
- Optional ability to let another program service establish connections
- To read a banner from the port
- Encrypted file transfer
- Command Line Chat Server
General Syntax :
nc [options] host port
Getting start with Netcat :
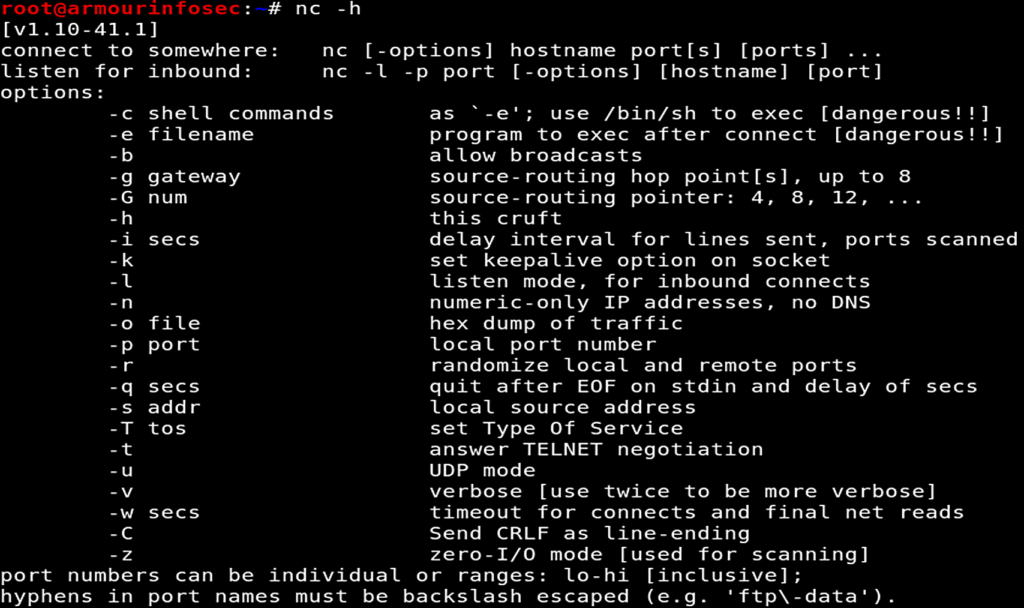
Netcat can be used from any directory. Let’s start with the basic option which will show us the help page by the following command.
nc -h
Port Scanning :
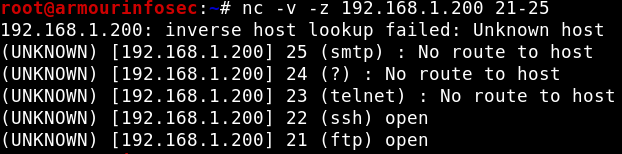
One of the most common uses for netcat is as a Port Scanner. It can be used to know which ports are open and running services on a target machine. It can scan a single or multiple or a range of open ports.
We will use -z option to perform only scan and -v option enables verbose mode options for a port scan like below.
nc -v -z 192.168.1.200 80
nc -v -z 192.168.1.200 21-25
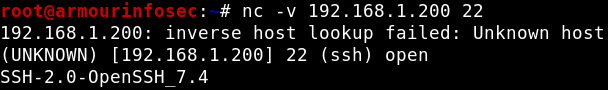
Banner Grabbing :
Netcat can be also used for grabbing service banner viz. Service Version, Status etc. To grab the target port banner from netcat, use the following command :
nc -v 192.168.1.200 22
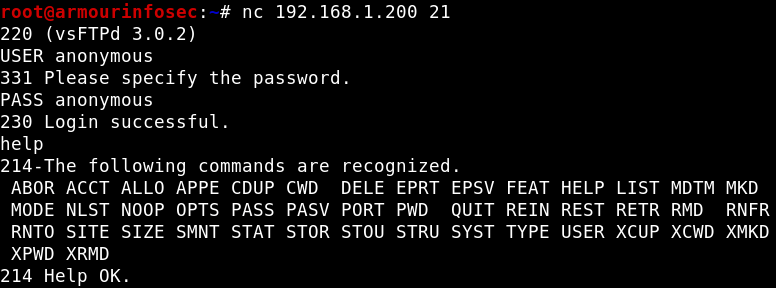
Connecting to a Server :
Here, we will connect a FTP Server with the IP Address 192.168.1.200. To connect to the server at a specific port where a particular service running. In our case, the port is 21 i.e. FTP.
nc 192.168.1.200 21
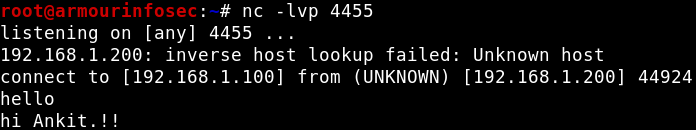
Command Line Chat Server :
Netcat can also be used to communication between two users. We need to establish a connection before chatting. For this we will need need two devices. One will play the role of initiator and other will be a listener to start the conversation. Once the connection is established, communication can be done from both ends.
User 1
OS: Kali Linux
IP Address: 192.168.1.100
Role: Listener
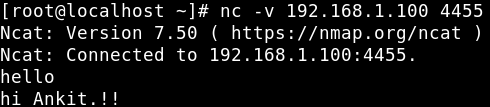
User 2
OS: CentOS
IP Address: 192.168.1.200
Role: Initiator
On User 1, we will start a listener on port 4455 using options -l for listen, -v verbose mode, -p for port
nc -lvp 4455
On User 2, we will create an initiator by providing IP address of listener followed by the listener port.
nc -v 192.168.1.100 4455
Transferring Files with Netcat :
Netcat can also be used to transfer files, both text and binary, from one computer to
another. Here we will create a scenario where we will transfer a file from a Kali system to Windows system.
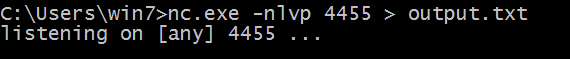
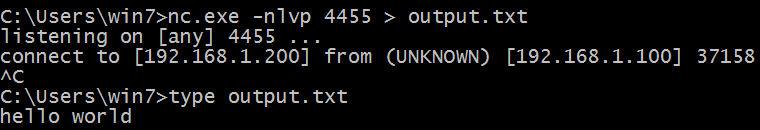
On the Windows system, we will set up a netcat listener on port 4455 and redirect any
incoming input into a file called output.txt.
nc.exe -nlvp 4455 > output.txt
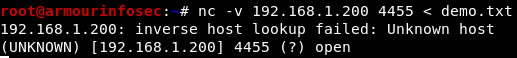
On the Linux system, we will push the file to the Windows system through port 4455:
nc -v 192.168.1.200 4455 < demo.txt
The connection which will be received by netcat on the Windows system as shown below:
Randomize Port :
If we can’t decide our very own port to establish a Netcat connection. Then we can use a special -r parameter which gives us randomize local port.
nc -lv -r
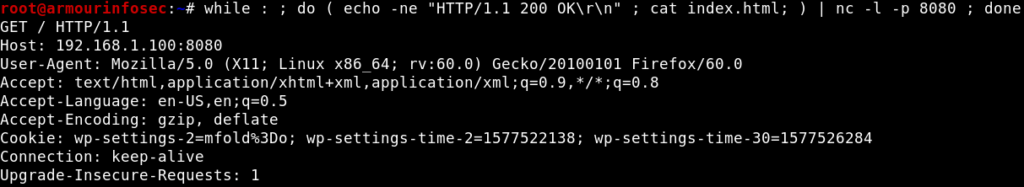
Simple Web Server with Netcat :
Netcat can be used as a simple web server. Actually, web servers are very simple if there are no special configuration requirements. Web servers only send HTML pages over HTTP protocol.
while : ; do ( echo -ne "HTTP/1.1 200 OK\r\n" ; cat index.html; ) | nc -l -p 8080 ; done
Remote Administration with Netcat :
One of the most useful features of netcat is its ability to do command redirection. Netcat can take an executable file and redirect the input, output, and error messages to a TCP/UDP port rather than the default console.
To further explain this, consider the cmd.exe executable. By redirecting the stdin, stdout, and stderr to the network, we can bind cmd.exe to a local port. Anyone connecting to this port will be presented with a command prompt belonging to this
computer. To further drive this home, consider the following scenario, involving Windwos and Kali.
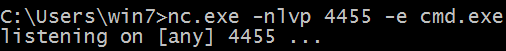
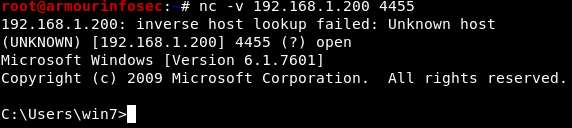
First, we will start a listener on Windows system for remote connection which will take place from Kali.
nc.exe -nlvp 4455 -e cmd.exe
On Kali when we will hit the listener port of Windows, we will get its Command Shell.
nc -v 192.168.1.200 4455