WordPress User Enumeration
These 10 enumeration techniques are a very fast way to identify users of a WordPress installation. With valid usernames effective brute force attacks can be attempted to guess the password of the user accounts.
Introduction to WordPress Security
There are many common attack vectors that hackers use to attack a WordPress website. In this article we expose many of the common avenues for attack. By revealing these, you can help build your website’s defenses against WordPress attacks.
There are some great guides available on securing a WordPress installation, this article is not intended to repeat those. To get started with securing a WordPress installation, try the excellent guide on wordpress.org or the comprehensive guide on the OWASP site.
It is noteworthy that in a managed WordPress hosting service, some of the attacks (and mitigation) listed below will be the responsibility of the hosting provider. If you are self hosting then security and maintenance is your responsibility. Ready to start? Grab our hoodie and start hacking!
In this article we are going to discuss several ways to identify the valid usernames of any WordPress website.
Table Of Contents:
1.Usernames enumerating through the Author Archives
2.WordPress Enumeration via JSON API
3.WordPress Enumeration via the Login Form
4.Enumerating WordPress Core Version
5.WordPress Plugin (and version) Enumeration
6. WordPress Theme Enumeration
7.Directory Indexing
8.Server Vulnerability Testing
9.WP Scan
10.Nmap NSE Scripts for WordPress
1.Enumerate Usernames Through the Author Archives :
In many WordPress installations, it is possible to enumerate WordPress usernames through the author archives, including the admin username. To access the author archives, we just need to add author=n (where n equals any integer) as a parameter to the WordPress home page, as shown below:
http://example.com/?author=1
The request will be automatically redirected by WordPress to its counterparts:
http://example.com/author/admin/
Using this method, we will be able to identify all the usernames by fuzzing the author parameter.
2.WordPress Enumeration via JSON API :
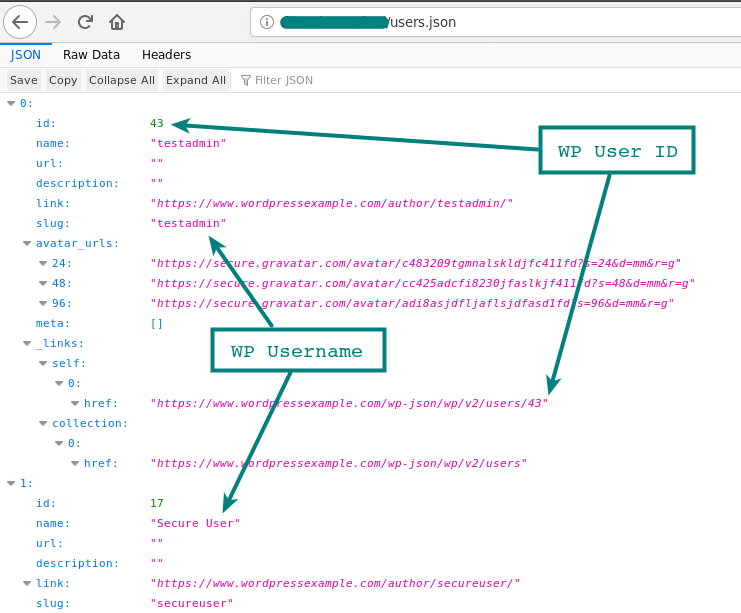
Using a json endpoint, it may be possible to get a list of users on the site. This was restricted in version 4.7.1 that shows only the user that has published a post and the user that has been configured. Prior to this version, all the users were shown by default.
https://wordpressexample.com/wp-json/wp/v2/users
User Enumeration via the JSON user Endpoint
3.WordPress Enumeration via the Login Form :
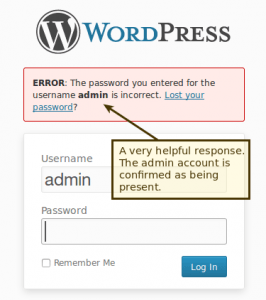
You must confirm valid users with the login form. Brute forcing the user name is possible using the login form as the response is different for a valid as opposed to an invalid account. Using a tool such as Burp Intruder in Burp Suite, we would load a list of possible usernames and cycle through HTTP POST requests to the WordPress login form, examining the response in each case.
A HTTP response that matches “invalid password” indicates that the username is valid. We could then move on to attacking the password using the same process with a common password list.
4.Enumerating WordPress Core Version :
Three simple methods can be used to determine the core version of WordPress.
4.1 Meta Generator
Check the HTML source of the page for a meta generator tag in the HEAD section of the HTML source. This example is taken from the source of a default WP install of the version 3.5.2 and of twenty twelve theme. From the source HTML:
<meta name="generator" content="WordPress 3.5.2" />
4.2 Version in readme.html
If the meta tag has been disabled, check for the presence of /readme.html from root of the install. Early versions of WordPress had the version right there at the top of the Read Me file. But the newer versions of WordPress have removed the version from the ReadMe file.
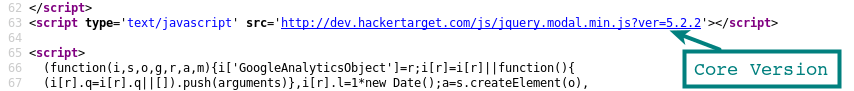
Version in HTML source of site.
In the HTML source, the version is often appended as a parameter on links to javascript and css resources that the page is loading. Depending on the plugin, this will not always be the case and sites that have minified js and css may not have all this information leaks present.
4.3 Security Vulnerabilities in WordPress Core
If an attacker finds a site with an older WordPress Core version, this may be directly exploitable via a security vulnerability in the WordPress core, In addition, it is a clear indication that the site is not well maintained. In a poorly managed site, other components (plugins / themes) may not have been updated; in this case, the chance of a successful attack has increased considerably.
5.WordPress Plugin (and version) Enumeration :
During WordPress Plugin Enumeration, we attempt to find as many installed plugins as we can (even those that are disabled). The knowledge of the installed WordPress plugins may allow us to identify the version and research whether it is vulnerable to known exploits.
Passive analysis: It can be used to find plugins through regular HTTP requests to the WordPress site.
Active enumeration: It is more aggressive and usually involves using a script or tool to perform hundreds or even thousands of mostly invalid HTTP requests.
Reading through the HTML source of the WordPress site can reveal installed plugins through javascript links, comments and resources, such as CSS that are loaded into the page. These are the easiest plugins to discover and require no aggressive testing of the target site. Even the HTTP headers can reveal information such as the X-Powered-By header that reveals the presence of the W3-Total-Cache plugin. Some plugins do not leave traces in the HTML source; to find all the installed plugins you have to be more aggressive. A number of tools can brute force known plugin lists from the path /wp-content/plugins/ * plugin to test * /. The web server response will usually reveal valid directories (often with HTTP 403) as opposed to unknown directories on the web server with its HTTP response code.
Once you have a list of plugins that are present on the site, your WordPress scanner or manual requests can be used to determine the version of the plugin. In the readme.txt, we can see the version of the plugin. Compare this against known exploits and we can get a good idea if the site is vulnerable without actually throwing the exploit.
6. WordPress Theme Enumeration :
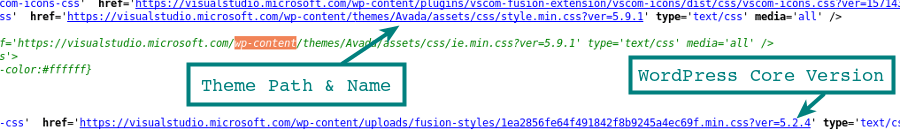
WordPress themes can contain vulnerabilities that might expose the site to compromise. Themes are collections of PHP code with HTML and CSS resources. More complex themes have more included components and are more likely to introduce security vulnerabilities. The enumeration of the theme is similar to the detection of plugins. The theme path is often visible in the HTML of the page source. The CSS file getting loaded from the theme will often reveal the path. With the path we have the theme name, and we can load the readme.txt to confirm the theme in use and its version.
curl http://examplewp.com/wp-content/themes/Avada/readme.txt
An important consideration when testing for vulnerable WordPress Themes (and plugins) is that a theme that is installed yet not active may still have code that is accessible and vulnerable. This is why brute force testing for theme paths is an important step when assessing an unknown WordPress installation.
7.Directory Indexing :
Directory indexing enabled on plugins directory. Directory indexing is a function of the web server that allows you to view the contents of a directory in the web accessible path. Viewing the contents of a directory allows an attacker to gather valuable information about the installation such as installed plugins and themes without the need to brute force the paths.
To check for directory indexing, you can browse to folder locations and see if you get a response that includes “Index Of” and a list of folders / files. Common locations to check would be:
/wp-content/ /wp-content/plugins/ /wp-content/themes/ /uploads/ /images/
8.Server Vulnerability Testing :
In this phase, we move into testing network services rather than direct testing of the WordPress installation. Port scanning is the standard technique for the discovery of network services running on the server.
Services that might be present on a WordPress host:
MySQL Server Remotely Accessible (port 3306)
CPANEL administration login portal (port 2082 / 2083)
Webmin administration (port 10000)
FTP service for file system access
SSH for remote control
Other web services with admin or other sites (port 8080 / 8888 etc)
Any of the above services may allow access to or control of the server through either a security vulnerability or a compromised password. Port scanning can be conducted using the excellent Nmap Port Scanner or an alternative security tool. Carrying on from our enumeration of network services using the port scanner, we could run vulnerability scans against the discovered services to identify exploitable services or other items of interest.
8.1 Nikto Vulnerability Scanner
Nikto is another vulnerability scanner that focuses on the discovery of known vulnerable scripts, configuration mistakes and other web server items of interest. The Nikto tool has been around for many years yet still finds a place in the penetration testers toolbox. Tools such as this throw tens of thousands of tests against the target in an attempt to discover known vulnerabilities and other low hanging fruits. It is a noisy process filling the target system logs with 404’s and other errors. Not recommended if you are going after a target ninja style (pentest / red team).
9.WPScan :
WPScan is a popular WordPress security testing tool that ties many of these simple enumeration techniques together, enabling users to quickly enumerate a WordPress installation. It has a commercial license that restricts the use for personal testing of WordPress sites and non-commercial usage.It attempts to identify users, plugins, and themes, depending on the selected command line options, and also show vulnerabilities for each of the discovered plugins.
https://github.com/wpscanteam/wpscan
10.Nmap NSE Scripts for WordPress :
Nmap comes bundled with NSE scripts that extend the functionality of this popular port scanner. A few of the Nmap NSE scripts are particularly helpful for enumerating WordPress users, plugins, and themes using the same techniques we have previously discussed. The best thing about this option is that if you have Nmap installed, you already have these scripts ready to go.
┌─[root@Dasagreeva]─[/usr/share/nmap/scripts] └──╼ #ls -lha |grep wordpress -rw-r--r-- 1 root root 5.0K Nov 26 14:51 http-wordpress-brute.nse -rw-r--r-- 1 root root 11K Nov 26 14:51 http-wordpress-enum.nse -rw-r--r-- 1 root root 4.6K Nov 26 14:51 http-wordpress-users.nse