Introduction of Mobile Forensic
Today’s smartphones are used less for calling and more for socializing. This has resulted in smartphones holding a lot of sensitive data about their users. Mobile devices keep the user’s contacts from a variety of sources (including the phone, social networks, instant messaging, and communication applications), information about phone calls, sent and received text messages, and e-mails and attachments. There are also browser logs and cached geolocation information; pictures and videos taken with the phone’s camera; passwords to cloud services, forums, social networks, online portals, and shopping websites; stored payment data; and a lot of other information that can be vital for an investigation.
Within mobile phones, smart phones are very much becoming the norm. Improvements in the computing power and data storage of these devices enable us to perform a wide range of activities.We are increasingly becoming dependent on these mobile devices for most of our activities. Apart from performing routine tasks such as making calls, sending messages, and so on, these devices also support other activities such as sending e-mails, surfing the Internet, recording videos, creating and storing documents, identifying locations with Global Positioning System (GPS) services, managing business tasks, and much more. In other words, mobile devices are now a repository of sensitive personal information, containing a wealth of user data.
Mobile Forensic
Mobile device forensics is a branch of digital forensics which deals with extracting, recovering and analyzing digital evidence or data from a mobile device under forensically sound conditions. Simply put, it deals with accessing the data stored on devices which includes SMS, contacts, call records, photos, videos, documents, application files, browsing history and so on, and also recovering data deleted from devices using various forensic techniques. It is important that the process of recovering or accessing details from a device is forensically sound, if it has to be admitted in a court of law and to maintain the integrity of the evidence.
Why we need Mobile Forensic ?![]()
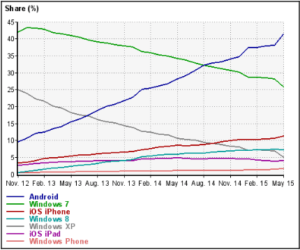
The importance of mobile forensics is hard to underestimate. Back in 2012, over 70% of web page requests originated from desktop and laptop computers (Windows 7 and Windows XP being the most popular systems). In May 2015, only 43% of requests come from desktop operating systems, while 54% of the traffic comes from Android, iOS, and Windows phone devices. If you look at the following graph, the trend is clear-the proportion of time the users spend with desktop computers is falling, while the use of mobile devices is rising.
The Mobile Forensic approach
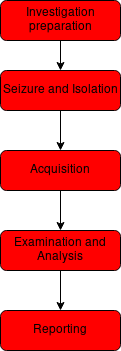
Once the data is extracted from a device, different methods of analysis are used based on the underlying case. As each investigation is distinct, it is not possible to have a single definitive procedure for all cases. However, the overall process can be broken into five phases as shown in the following diagram.
Investigation preparation:
This phase begins when a request for examination is received. It involves preparing all of the paperwork and forms required to document the chain of custody, ownership information, the device model, its purpose, the information that the requester is seeking, and so on. The chain of custody refers to the chronological documentation or paper trail, showing the seizure, custody, control, transfer, analysis, and disposition of physical or electronic evidence. From the details submitted by the requester, it’s important to have a clear understanding of the objective for each examination.
Seizure and Isolation:
Handling the device during seizure is one of the important steps while performing forensic analysis. The evidence is usually transported using anti-static bags which are designed to protect electronic components against damages produced by static electricity. As soon as the device is seized, care should be taken to make sure that our actions don’t result in any data modification on the device. At the same time, any opportunity that can aid the investigation should also not be missed.Handling the device during seizure is one of the important steps while performing forensic analysis. The evidence is usually transported using anti-static bags which are designed to protect electronic components against damages produced by static electricity. As soon as the device is seized, care should be taken to make sure that our actions don’t result in any data modification on the device. At the same time, any opportunity that can aid the investigation should also not be missed.Unlike PCs that can be either online or offline (which includes energy-saving states of sleep and hibernation), smartphones and tablets use a different, always-connected mods.
Tremendous amounts of activities are carried out in the background, even while the device is apparently sleeping. Activities can be scheduled or triggered by a large number of events, including push events from online services and events that are initiated remotely by the user.
Another thing to consider when acquiring a mobile device is security. Mobile devices are carried around a lot, and they are designed to be inherently more secure than desktop PCs. Non-removable storage and soldered RAM chips, optional or enforced data encryption, remote kill switches, secure lock screens, and locked boot loaders are just a few security measures to be mentioned.
The use of Faraday bags
Faraday bags are commonly used to temporarily store seized devices without powering them down. A Faraday bag blocks wireless connectivity to cellular networks, Wi-Fi, Bluetooth, satellite navigation, and any other radios used in mobile devices. Faraday bags are normally designed to shield the range of radio frequencies used by local cellular carriers and satellite navigation (typically the 700-2,600 MHz), as well as the 2.4-5 GHz range used by Wi-Fi networks and Bluetooth. Many Faraday bags are made of specially-coated metallic shielding material that blocks a wide range of radio frequencies.
With increasing user awareness on security and privacy, most of the devices now have screen lock enabled.
During the time of seizure, if there is a chance to do so, disable the pass code.Some devices do not ask the user to re-enter the pass code while disabling the lock screen option.If the device is unlocked, try to change the settings of the device to allow greater access to the device. Some of the settings that can be considered to achieve this are as follows:
- Enable USB debugging: Enabling this option gives greater access to the device through Android debug bridge (adb) connection.
- Enable stay awake setting: Enabling this option and charging the device will make the device stay awake which means that, it doesn’t get locked. In Android devices, this option is usually found under Settings | Developer options, as shown in the following screenshot
- Increase Screen timeout: This is the time for which the device will be active once it is unlocked. Depending on the device model, this time can be set up to 30 minutes. In most devices, it can be accessed under Settings | Display | Screen timeout.
Acquisition:
The acquisition phase refers to the extraction of data from the device. Due to the inherent security features of mobile devices, extracting data is not always straight forward. Depending on the operating system, make, and model of the device, the extraction method is decided. The following types of acquisition methods can be used to extract data from a device:
1. Manual acquisition: This is the simplest of all acquisition methods. The examiner uses the user interface of the phone to browse and investigate. No special tools or techniques are required here, but the limitation is that only those files and data that are visible through a normal user interface can be extracted. Data extracted through other methods can also be verified using this.
2. Logical acquisition: This is also called logical extraction. This generally refers to extracting the files that are present on a logical store such as a file system partition. This involves obtaining data types, such as text messages, call history, pictures and so on, from a phone. The logical extraction technique works by using the original equipment manufacturer’s APIs for synchronizing the phone’s contents with a computer. This technique usually involves extracting
the following evidence:
- Call Logs
- SMS
- MMS
- Browser history
- Peoples (phone call)
- Contact methods
- Contacts extensions
- Contacts groups
- Contacts phones
- Contacts setting
- External image media (metadata)
- External image thumbnail media (metadata)
- External media, audio, and misc. (metadata)
- External videos (meta data)
- MMS Parts (includes full images sent via MMS)
- Location details (GPS data)
- Internet activity
- Organizations
- List of all applications installed, along with their version
- Social networking apps data such as Whats App, Skype, Facebook, and so on.
3. Physical acquisition: This involves making a bit-by-bit copy of the entire flash memory. The data extracted using this method is usually in the form of raw data (as a hexadecimal dump),which can then be further parsed to obtain file system information or human readable data. Since all investigations are performed on this image, this process also ensures that original evidence is not altered.
4. File system acquisition: This is a logical procedure and generally refers to the extraction of a full file system from a mobile device. File system acquisition can sometimes help in recovering deleted contents (stored in SQLite files) that are deleted from the device.
Examination and Analysis :
In this phase, different software tools are used to extract the data from the memory image. In addition to these tools, an investigator would also need the help of a hex editor, as tools do not always extract all the data. There is no single tool that can be used in all cases. Hence, examination and analysis requires a sound knowledge of various file systems, file headers, and so on.
Reporting:
Documentation of the examination should be done throughout the process, noting down what was done in each phase. The following points might be documented by an examiner:
- Date and time the examination started
- Physical condition of the phone
- The status of the phone when received (ON/OFF)
- Maker, model, and operating system of the phone
- Pictures of the phone and individual components
- Tools used during the investigation
- Data documented during the examination
The data extracted from the mobile device should be clearly presented to the recipient so that it can be imported into other software for further analysis. In the case of civil or criminal cases, wherever possible, pictures of data, as it existed on the cellular phone, should be collected, as they can be visually compelling to a jury.