IP Address: It’s in general a name assign to a computer, address of a computer. It serves two principles: Host…
How to Protect Grub Boot Loader by Password in Kali Linux. GRand Unified Bootloader (GRUB) is a default bootloader in…
Before you lose or forgot your password and left with frustration and exasperation, you should know how to change or…
Firefox add-ons are useful for penetration testers and security analysts. These penetration testing add-ons helps in performing different kinds of…
Google offers special terms known as advanced operators to help you perform more advanced queries. These Operators, used properly, can…
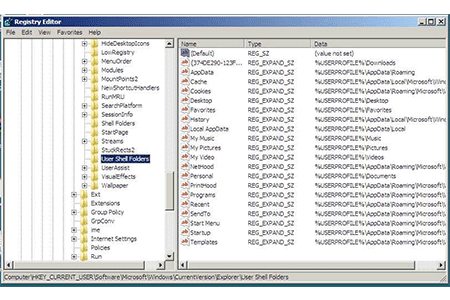
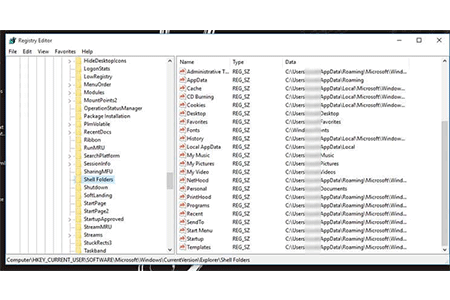
The windows operating system stores user profile information in a User Shell Folders. Windows stores the location of per-user special…
Special or shell folder in windows Shell folders in Windows are specific folders that are used as the default location…
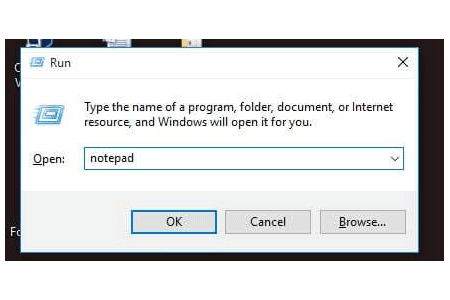
Run Commands for Windows Press Window + R, then type RUN command, then press enter. Run commands are just like…
John the Ripper John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS,…